HacktheBox (HTB) has provided another teachable moment with “RETIRED” HTB: ACCESS.htb; giving us the opportunity to develop existing skills, using cool tools and learning new concepts/techniques. Let’s jump in but before we do so…please read the warning below.

SPOILER ALERT!!!!!
Public Service Announcement

THIS IS ONLY FOR EDUCATIONAL PURPOSES. Access to this system by HTB VPN.
- Signup for HackTheBox Account.
- Acquire VPN credentials and authenticate.
- Test access to the system. Keep in mind RETIRED system access is ONLY allowed with PAID subscription. Check HTB for more details.
Reconnaissance
KeyPoint: THE BETTER YOU GET AT ENUMERATION, THE BATTLE IS HALF WAY WON.
After running NMAP with the following FLAG “-sC -sV -p- –open”, then output all format with “-oA“. Here is the results.
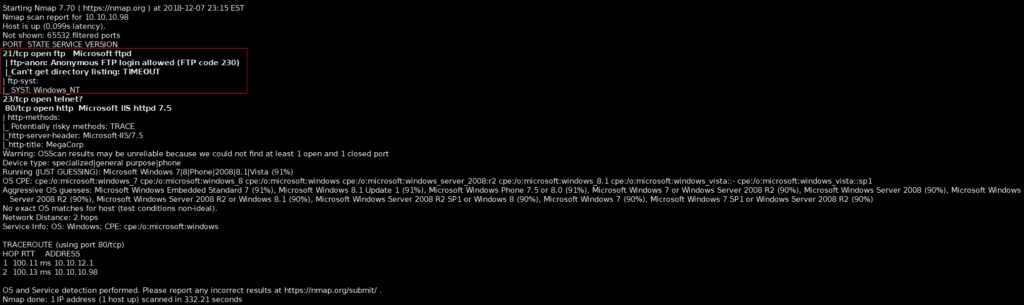
Discovered that FTP allows default credentials (i.e. Username: anonymous & Password: anonymous) by focusing on the FTP service, using the default credentials allowed access to the system.
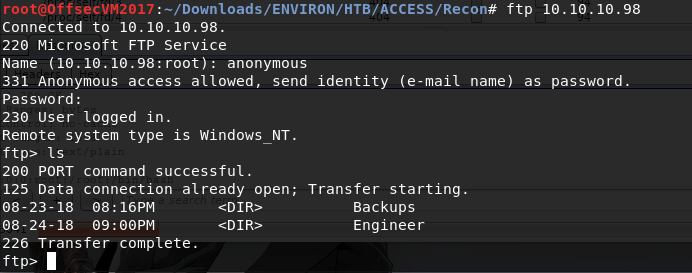
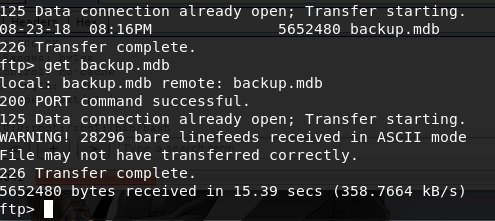
Browsing and grabbing files from the available directories.
Next, navigate to the web sever on HTTP port 80, which provides access to FTP service again just in a GUI format.
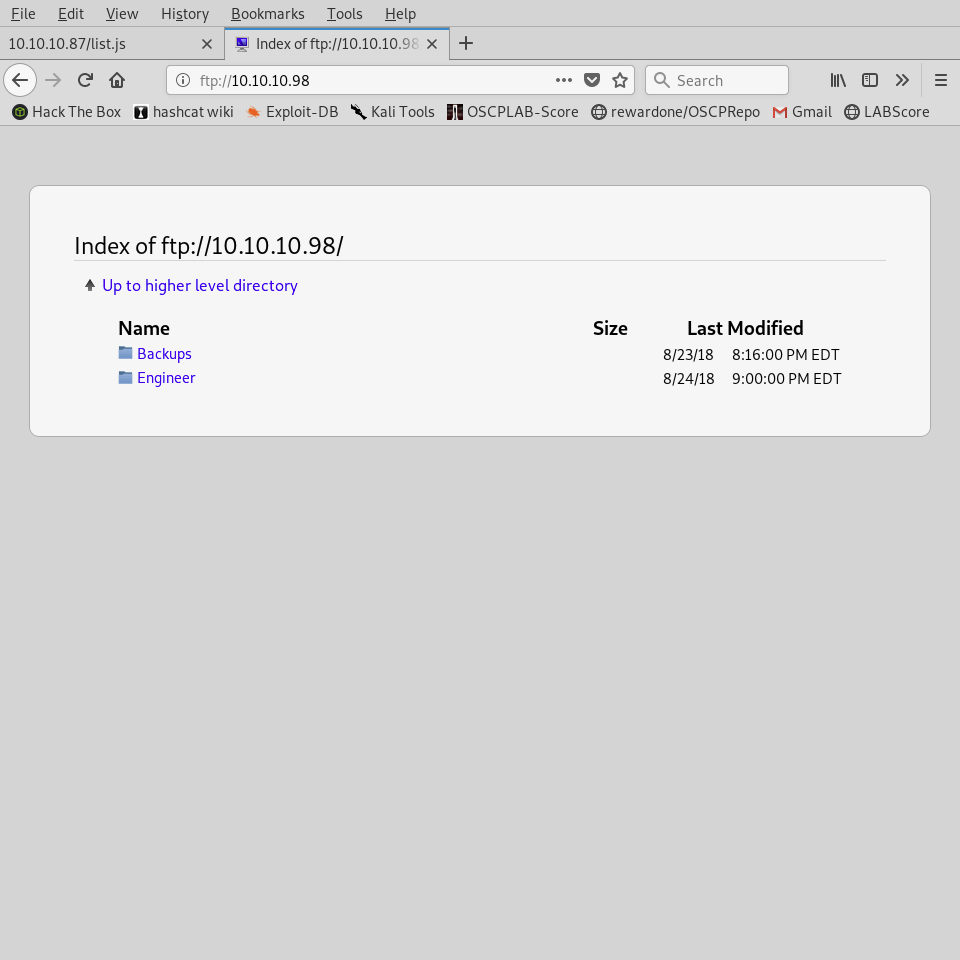
Retrieve Telnet credentials and used those credentials to authentication.
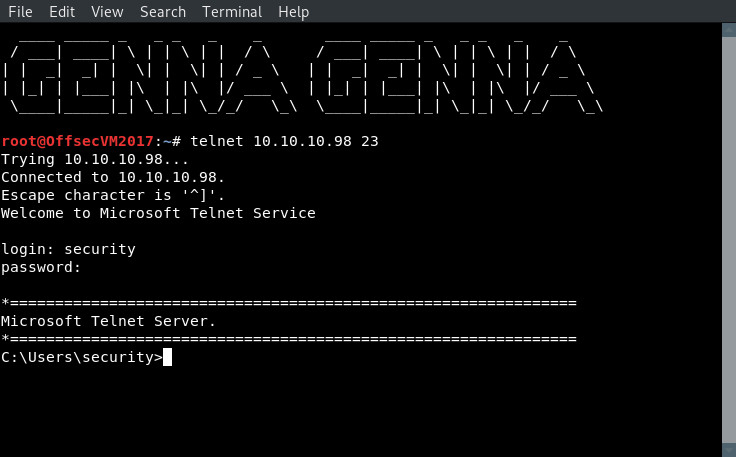
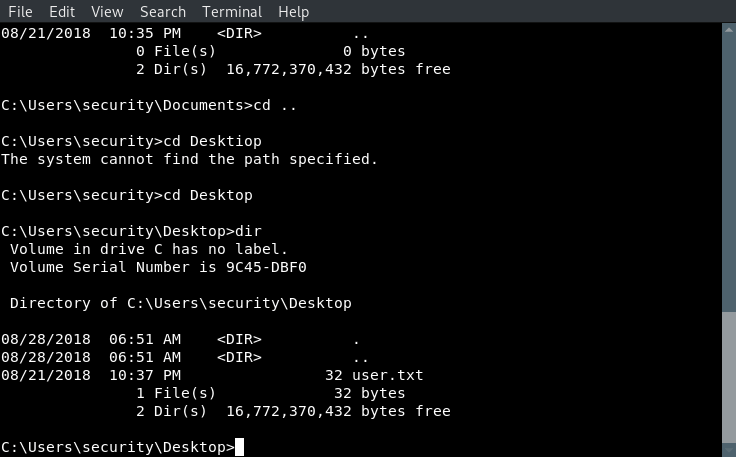
At this point, we have clear the user.txt flag and need to find a path to privilege escalation (PRIVESC). Performing POST-Exploitation reconnaissance, an aa.txt file was found that gave keep details on how to achieve PRIVESC.
Date of last applied patch – just use public exploits if not patched:
Files that may contain Administrator password – you know what to do with this one:
“C:\Windows\Panther\Unattend.xml”
C:\Windows\panther\setupinfo
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Config\web.config
Checking AlwaysInstallElevated – install *.msi files as NT AUTHORITY\SYSTEM – exploit/windows/local/always_install_elevated:
Checking privileges – rotten potato:
Checking if WSUS uses HTTP – eg. WSUXploit:
Services with space in path and not enclosed with quotes – if you have permissions run executable from different directory – exploit/windows/local/trusted_service_path:
Checking if SCCM is installed – installers are run with SYSTEM privileges, many are vulnerable to DLL Sideloading:
Not Installed.
—————————————————–
Checking possibly weak permissions for administrators group:
Services and their registries permissions – change BINARY_PATH_NAME of a service or path to the binary in the registry:
Take advantage of the Files that may contain Administrator password attack, the root.txt file was successfully written to our “rootqwerty.txt” file successfully.
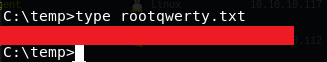
And just like that we HACKTHEBOX.




