Jetty 1 – VulnHub WriteUp
It’s that time again when we challenge our skills in an effort to learn something new daily and VulnHub has provided yet again. Jetty 1 by MrSquid; giving us the opportunity to pay attention to details and use cool tools.…

It’s that time again when we challenge our skills in an effort to learn something new daily and VulnHub has provided yet again. Jetty 1 by MrSquid; giving us the opportunity to pay attention to details and use cool tools.…

On a recent internal penetration test, the clients goals were to gauge what an internal user or attacker could achieve with user level access to their network. In these cases you want to look for known exploits, weak passwords and…

We do not know all things Penetration Testing or Hacking but what we do know is OUR WILLINGNESS to constantly share what we know with you. They are probably better ways to hack the VulnHub WarZone2 Virtual Machine (VM) by…

As a Penetration Tester, the constant need to practice our skills is required to improve our penetration testing (PT) abilities. Thus making this process a deliberate and willful one in order to be better at our craft. As a result,…
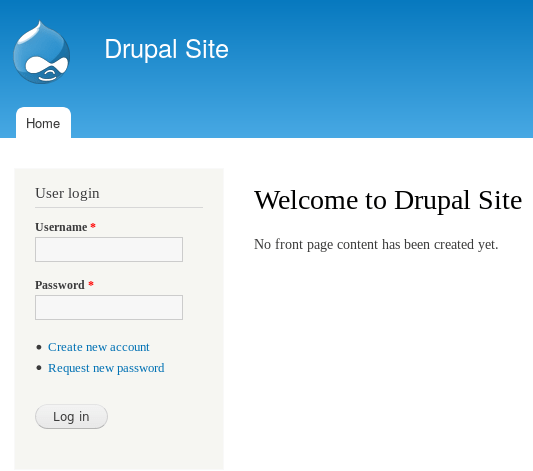
From the people who brought you WHAT THE CTF, CyberGuider is please to present its official walkthrough of DC1:1 from VulnHUB. This system was a lot of fun and shows that simple misconfigurations can cause the system to be compromised.…
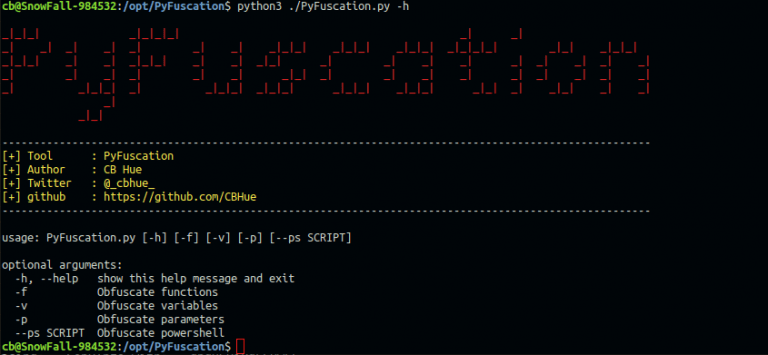
In the last post we found that Windows Defender uses a black list to stop known hacking tools such as Mimikatz. We were able to easily bypass the restriction with some word replacements but it took time, trail and…

I was on a penetration test when i was able to acquire a set of admin credentials. This wasn’t a red team engagement, so there was no issues lighting up their AV with some of our tools but I always…

Most of the time I’m binge watching Netflix, Amazon Prime, Hulu, or some other instant gratification media platform. But on the rare occasion that I’m out in these streets and talking to other professionals, the conversation always ends up at…

The average computer user does not think much about the amount of information he or she shares with others whether in-person, online or at random venues. They just want to be seen and heard because that is how the world…

Often times as information technology (IT) security professionals (a.k.a. Security Pros), we meet others who are interested in what we do for a living. The transfer of knowledge serves as a good way to promote IT security and often kick-starts…